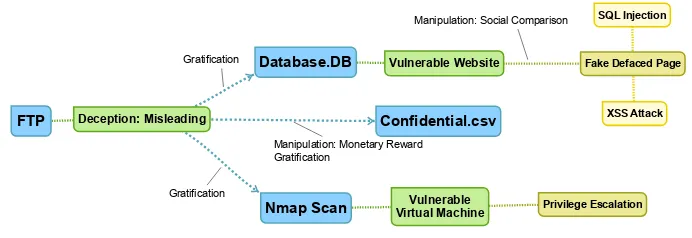
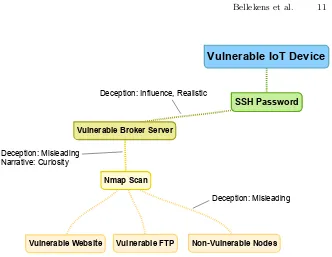
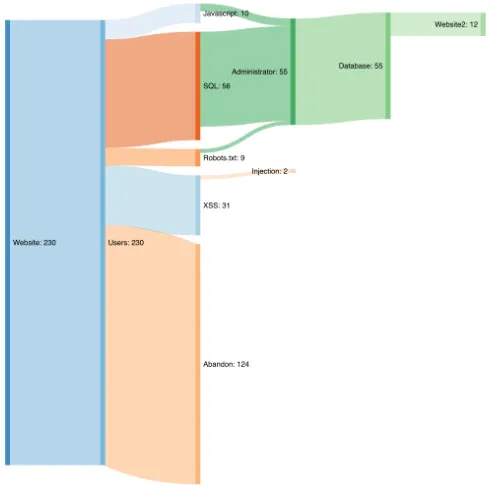
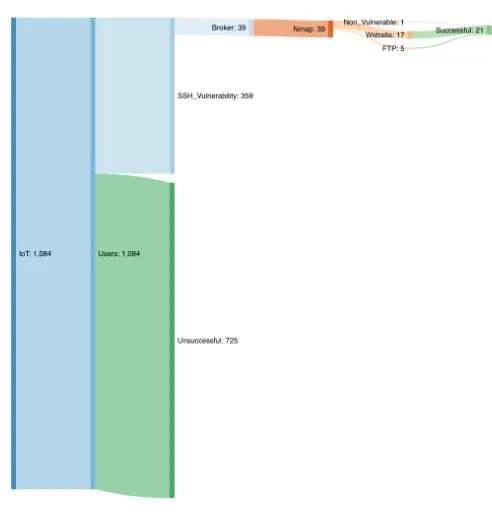
From cyber-security deception to manipulation and gratification through gamification
Full text
Figure

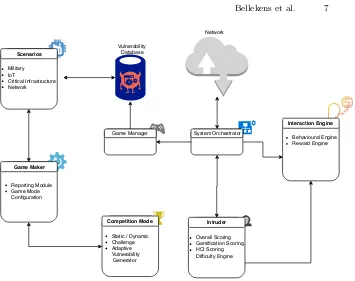

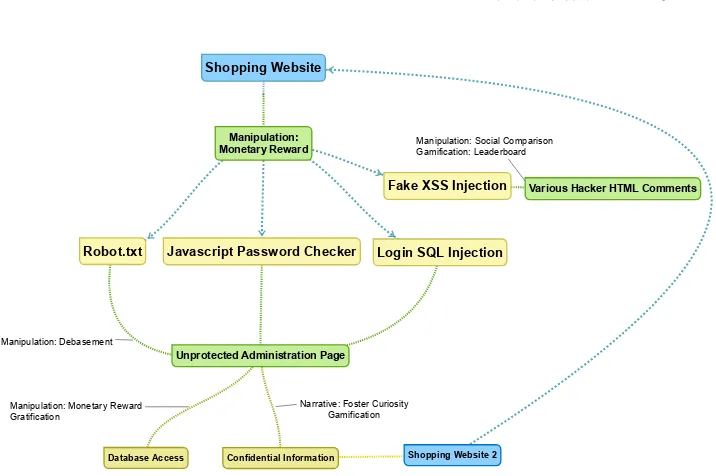
Related documents
Conversely, 43.7% of all respondents who misused prescription drugs met criteria for alcohol dependence, problem gambling, and (or) had used illicit drugs in the past year..
UPnP Control Point (DLNA) Device Discovery HTTP Server (DLNA, Chormecast, AirPlay Photo/Video) RTSP Server (AirPlay Audio) Streaming Server.. Figure 11: Simplified
We tested a hypothesis that both individual-level risk factors (partner number, anal sex, condom use) and local-network features (concurrency and assortative mixing by race) combine
For instance, in choice situations 1, 4 and 6, society A presents a higher level of absolute income, while society B offers a bundle of more favourable positional measures (i.e.
Large deviations of the this antioxidant activity are considerable, as well as content of phenolic compounds between pollen grains taken from different plant species
14 When black, Latina, and white women like Sandy and June organized wedding ceremonies, they “imagine[d] a world ordered by love, by a radical embrace of difference.”
• C.1 Number of Students Enrolled in Nursing Fundamentals Course in the Fall Two Academic Years Previous. For example, if the current academic year is 2007-2008, then the fall
• Leaders need to ensure that all staff adopt leadership roles in their work and take individual and collective responsibility for delivering safe, effective, high- quality