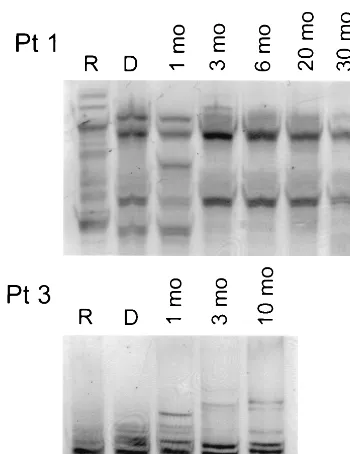
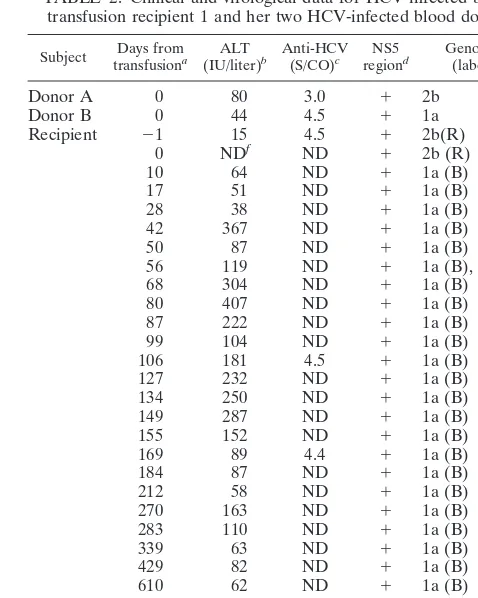
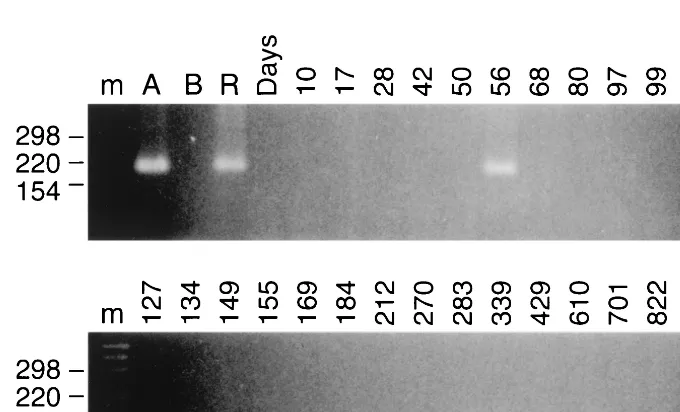
Exposure of Hepatitis C Virus (HCV) RNA-Positive Recipients to HCV RNA-Positive Blood Donors Results in Rapid Predominance of a Single Donor Strain and Exclusion and/or Suppression of the Recipient Strain
Full text
Figure
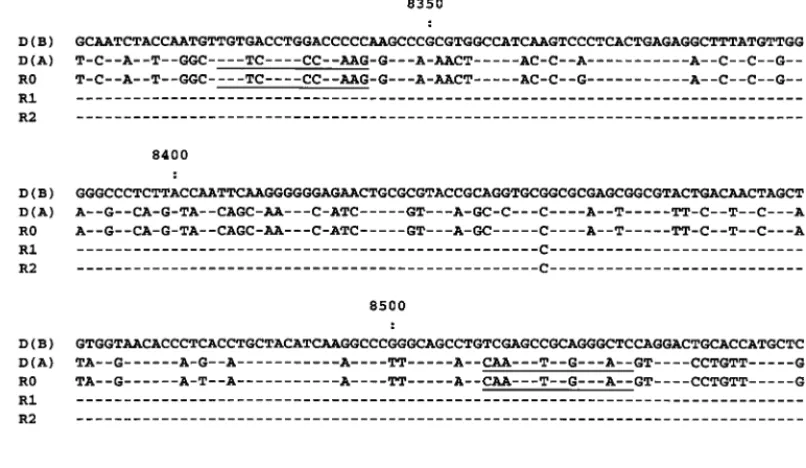
![FIG. 4. Nucleotide sequence alignment of the NS5 fragments of HCV recovered from the recipient prior to transfusion (R0) and donor A[D(A)], and amplified from a follow-up serum sample with primers specific for type 2b sequences (Fig](https://thumb-us.123doks.com/thumbv2/123dok_us/502667.69469/5.612.109.497.77.312/nucleotide-alignment-fragments-recovered-recipient-transfusion-amplied-sequences.webp)
Related documents
However, following 6 months of daily open access ethanol self-administration, when the responses to pharmacological challenges had moved toward their baseline levels of
Taxable Wage Calculation: When calculating the amount of tax- able wages for the quarterly contribution report in the year of the transfer from another state, an employer should
This paper is based on the understanding that most of these difficulties can be managed by using queuing model to determine the waiting line performance such
We therefore present a methodology to generate several synthetic traffic traces from a single real trace of packets, by carefully group- ing packets belonging to the same flow
The model, which prevailed until the early 1990s – whereby large banks used to be net borrowers from the rest of the system, and dealt directly with a number of small players at
Regardless of what preservice teachers initially believe about the teaching of writing and the importance of technology within the process, it is evident that the time
THE INTERNATIONAL REACH OF THE INTERNET2 NETWORK Current Networks
The malicious actors used a powerful combination of Network Time Protocol (NTP) reflection and Domain Name System (DNS) reflection as the main attack vectors, which also