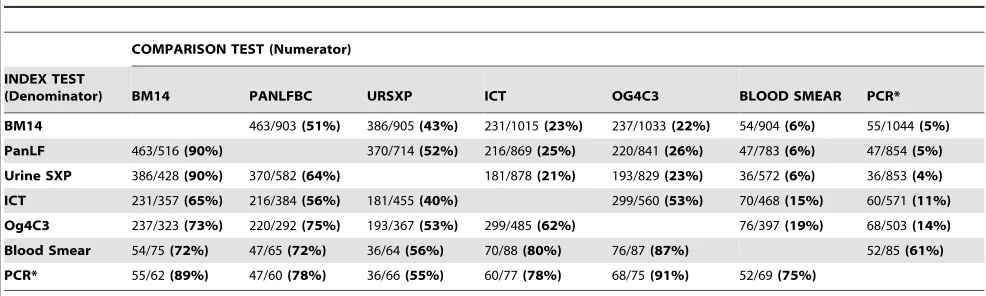
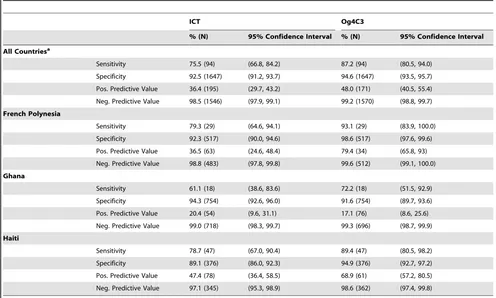
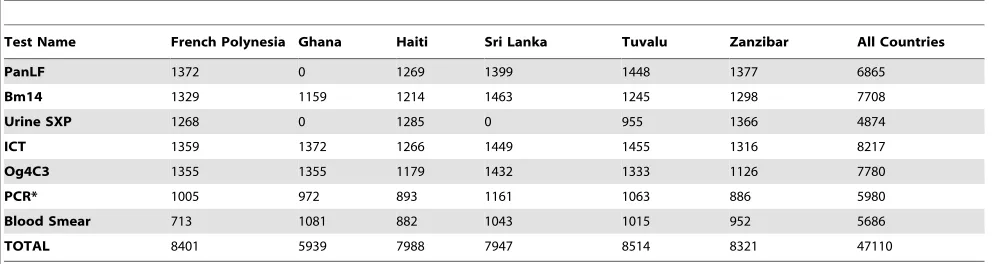
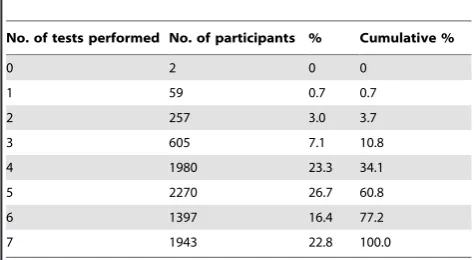
A multicenter evaluation of diagnostic tools to define endpoints for programs to eliminate bancroftian filariasis
Full text
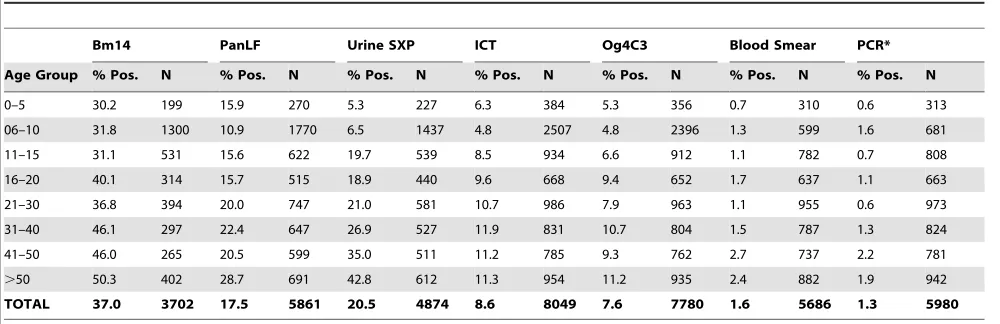
Figure

Related documents
The simulation results indicate that the proposed algorithm reduces buffer consumption by 14.58%~51.04% under diverse traffic patterns and VC depth, while keeping similar
The purpose of the current study was to use hydrothermal germination models and a soil energy and water flux model to evaluate intra- and interannual variability in seedbed
A SKIE (and SKIE-OTRU) scheme is considered CCA-secure with optimal threshold if two conditions hold: (1) given access to pk, a decryption oracle, and pairs (hsk i , usk i ) of
Key words: specialist, project based learning, project, authentic sources, self- education, linguistic knowledge, personality.. In modern conditions of the rapid development
Simi- lar to our study, previous enmity was observed at Ben- galuru [6] and at Aurangabad [10] whereas study at Ah- medabad [5] reported domestic quarrel (41%) followed by dispute
AGEP: acute generalized exanthematous pustulosis; ALDEN: algorithm of drug causality for epidermal necrolysis; BSA: body surface area; CMV: cytomegalovi‑ rus; Cys A: cyclosporine
AOR: Adjusted Odd Ratio; CI: Confidence Intervals; FG: Food Group; HAZ: Height-for-Age Z-scores; IYCF: Infant and Young Child Feeding; MDD: Minimum Dietary Diversity; OR: Odd Ratio;
To provide security for dynamic group system integrates Image based authentication and one time password to achieve high level of security. However existing system