1+N Network Protection for Mesh Networks: Network Coding Based Protection Using p Cycles and Protection Paths
Full text
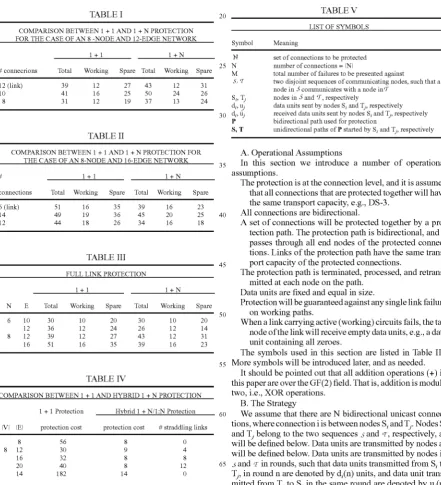
Figure


Related documents
The experiment started by soil sampling at four different rice field plots (Pokok Kenanga, PPK Fasa 3, PPK Fasa 1, and Sungai Burung Darat) in Balik Pulau rice field ecosystem..
2.8 There was ongoing contact between a number of agencies including health, Drugs services and Children’s Social Care during 2005 and 2006 with concerns focused on the impact
Strategies: Increase program awareness through community partnership and Increase the number of member and non YMCA member participation in program by 7% between 2018 to 2020
JCP&L provides the command and control of the storm restoration process within its service territory, but FirstEnergy controls mutual assistance, communications
(2017) Cardiolipin mediates membrane and channel interactions of the mitochondrial TIM23 protein import complex receptor Tim50. (2013) Structural changes in the mitochondrial
Because of the variations in etiology and severity of Mild Cognitive Impairment, in addition to the high comorbidity of Depression, it was postulated individuals in the Mild
A clinical team comprising medical doctors and public health nurses determined the follow-up CDR blindly to the previous CDR stages, baseline cognitive test scores, and MRI data Is
There are several actors involved in the decision-making processes on energy provision in the Kigeme refugee camps such as camp residents; MINEMA; UNHCR Rwanda; Refugee Exec-