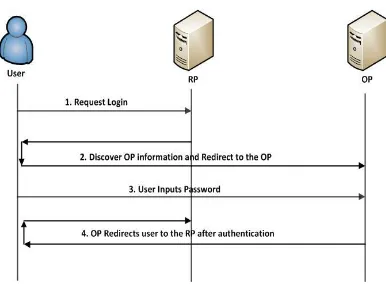
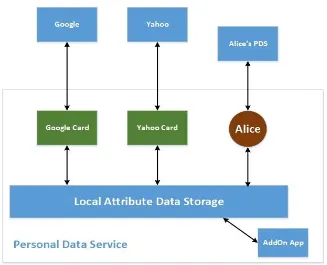
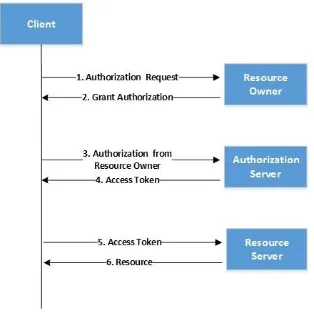
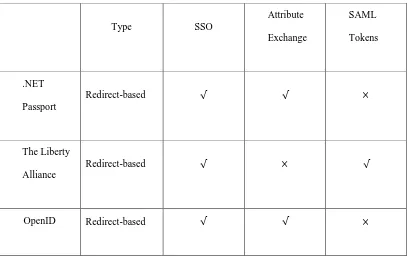
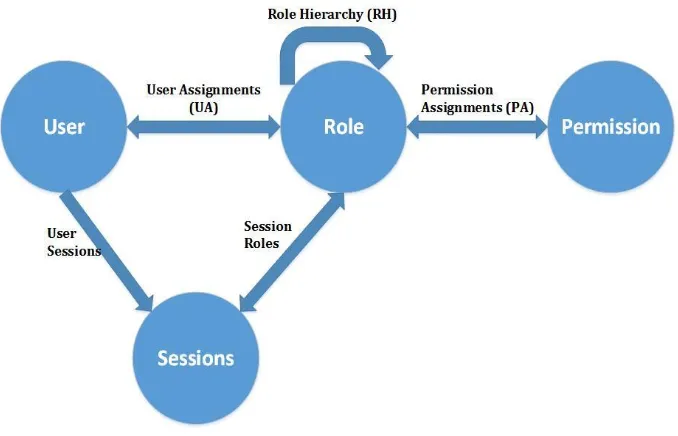
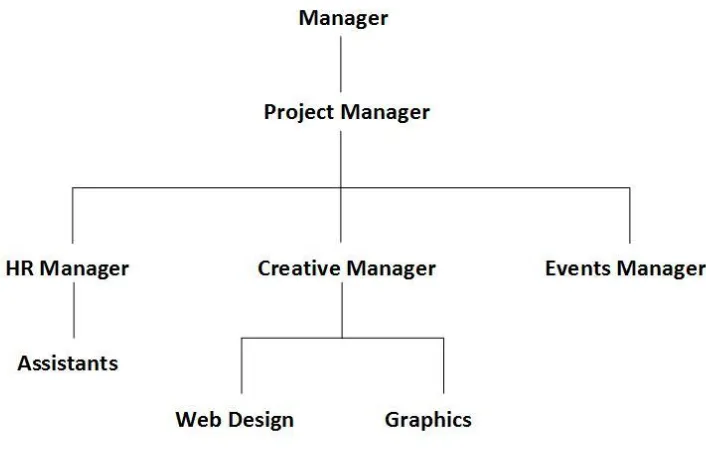
Context-Aware Attribute-Based Techniques for Data Security and Access Control in Mobile Cloud Environment
Full text
Figure
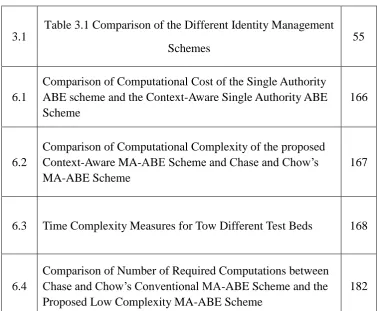
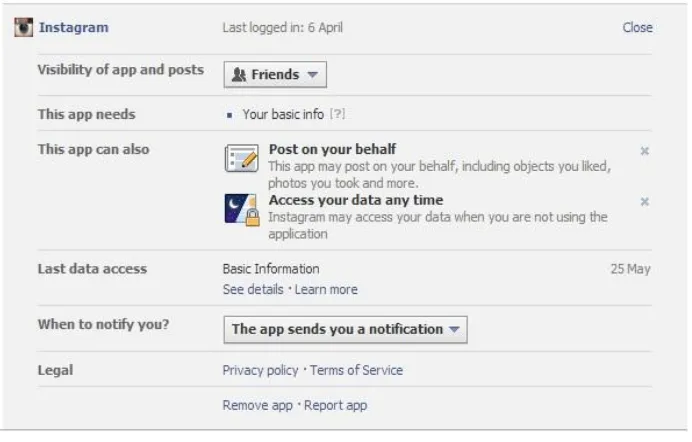
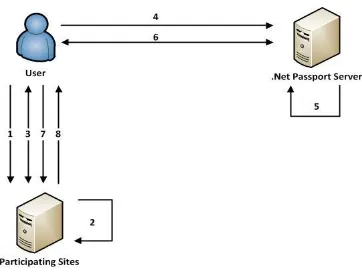
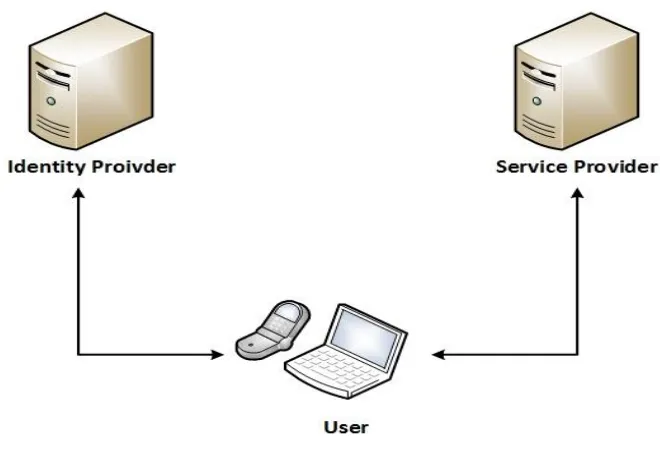
Related documents
Integrity matters Advisian 14 Integrity relevance Safety / Risk management Operations / Maintenance Integrity boundary Corrosion / condition Activities and
En efecto, así como los libertarianos ven en cual- quier forma de intervención del Estado una fuente inevitable de interferencias arbitrarias –con la excepción de aquella acción
ITXARO BORDA: MELANCHOLIC ,MIGRANCY AND THE WRITING OF A NATIONAL LESBIAN SELF 299 Contrary to her southern counterparts, she expresses a mournful melancholia, a migrant longing,
Because of this circumstances, the Spanish government has created several rules focused on minimizing the environmental impact caused by the construction industry and, in
Sector of activity: Heating, ventilation, air-conditioning and refrigeration systems, controls, services and sustainable solutions for residential, commercial, industrial, food
Chapter 7 Lab - Decimal, Binary, Octal, Hexadecimal Numbering Systems This assignment is designed to familiarize you with different numbering systems, specifically: binary,
Farmers who wanted to trade with the Swahili people walked to the coast and back with all the goods they took and received from trading.. They were very clever and used the stars