193 (Cissp)an Introduction To Computer Security (The Nist Handbook) [ PUNISHER ] pdf
Full text
Figure


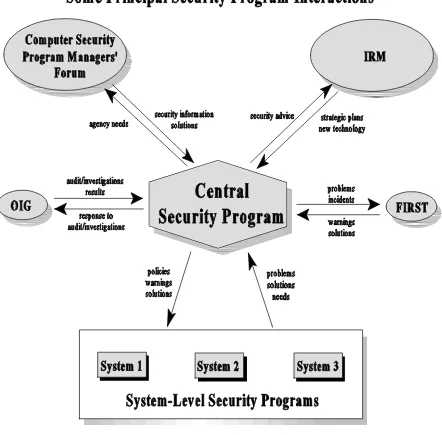
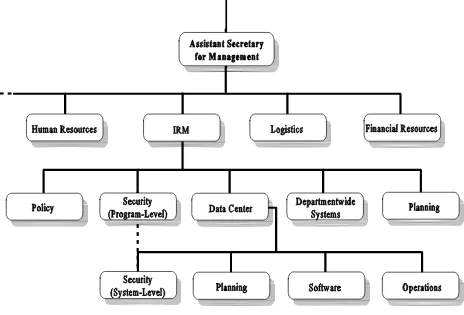
Outline
Related documents
4 Operation at 1.55 µm optical power input (a) Optical Field propagation in the DOS architecture (b) cut view of the output section, graph showing electric field intensity
The California FreshWorks Fund (FreshWorks) is announcing the availability of $2 million in loan capital, as well as companion grants and technical assistance resources, for
All other patients received 5-FU at the planned dose during week 1 of CRT, but five patients were given no further 5-FU in week 5 (two because of low blood counts, one due
In addition, within the dual-task conditions, serial recall was more accurate when digits and sound were presented at the same speed, but significantly fewer numbers were
District health boards will plan most health and disability support—that is, social care—services (although some services will be funded nationally by the Ministry of Health) and
Levels (optical densities ⫹ SEM ) of antibodies recognizing periodate-resistant peptide epitopes during chronic infection of 3 individual chimpanzees, namely, IgG antibodies
screening follow-up, including triggers for referral to (campus and/or off- campus) sleep medicine providers. Recommendation 9: Provide evidence- based sleep education to
Topical anti-acne treatment with other medicinal products supplementary to nadi- floxacin cream was documented in 150 patients (27.0%) and 57 patients (10.3%) received




