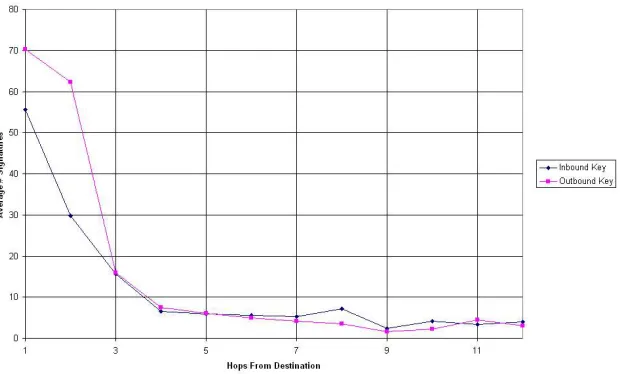
Communities of Trust in Pervasive Wireless Networks (Mini Thesis)
Full text
Figure



Related documents
Choose the Server Group you created above -> on the RHS click on new button choose the radius server from the drop down menu -> Add Server -> Apply... As to check whether
After that, the energy impacts of the retrofit strategies during the life cycle were assessed and compared with the energy savings in the use phase, allowing to calculate the
Significance narrative: The former Herald Building was built in 1913, according to the 1938 King County property record card, at the southeast corner of Griffin Avenue and Wells
Configure Apache HTTP Server so that it acts as a RADIUS client and forwards the authentication request to SafeNet Authentication Service. Open the httpd.conf file located
As the F5 FirePass can perform authentication to an external service using the RADIUS protocol, we will place the IDENTIKEY Server as back-end service for the F5 FirePass
As the Connectra can authenticate to an external service with RADIUS, we will place the IDENTIKEY Server as middleware or as back-end service, to secure the authentication with
As the ASA can perform authentication to an external service using the RADIUS protocol, we will place the IDENTIKEY Server as back-end service, to secure the authentication with
A transceiver had a program pulse input and output terminal, a clear-correct switch (to clear or not clear its content after a cycle; it could also be used to round off