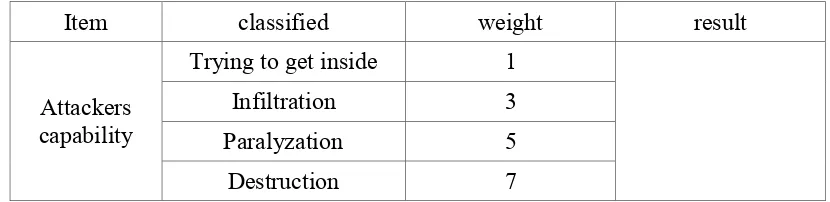
A study on security level management model for information system
Full text
Figure

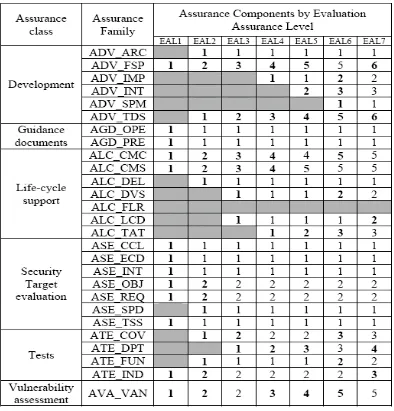

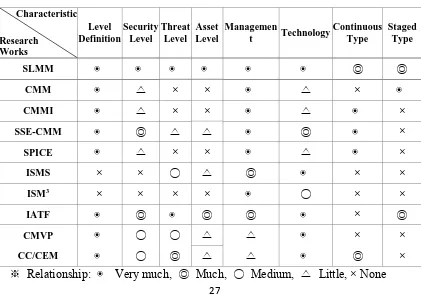
Related documents
The next day, President Ma resigned as Chairman of the KMT (Chyan, 2014). As a barometer for the Presidential and Legislative elections in 2016, pundits are betting on a return
Musical interventions with adults with cognitive impairments have received increased attention over the past few years, such as the value of personalized music listening in the
A GPN was also funded by Health Education England (East Midlands) (HEEM) to visit practices one day a week to help staff offer placements to nursing students, to undertake
Total distributions paid to Enhanced Debentureholders to date 42,659 % recovery across all Debentureholders (based on Debentureholder registry as at date of appointment) 66.2%
[r]
The figure present the market variables, accounting ratios, and the microstructure variables for the bankrupt and nonbankrupt firms from one year before bankruptcy (year 1) to
The aim of the paper is to examine Suzan Lori Park’s play, Venus to investigate ways in which black African women could be emancipated from discrimination,
Homework/Study Room with built in Desk Area, Double Door Closet, Bath featuring tile flooring, vanity stone countertop, shower over tub with tile surround, baseboard molding,