Efficient Implementations of Pairing-Based Cryptography on Embedded Systems
Full text
Figure

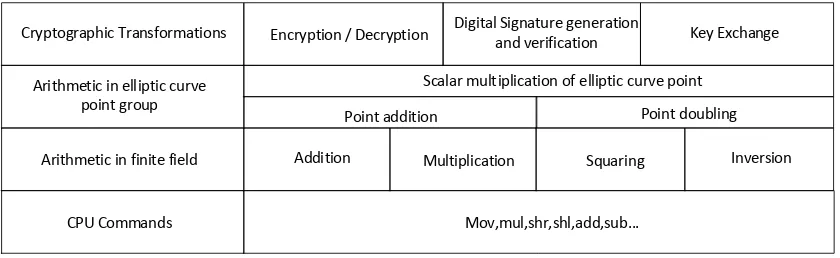

Outline
Related documents
variable is simple to compute, is objectively derived and has a defined framework that uses company specific information only which limits the influence of other
In this study, the in− fluence of the extract from the radix of Scutellaria baicalensis on the activity of ALT manifested itself as an increase in the activity of this enzyme in
The adverts were then grouped into five broad categories, namely: academic, archives and records management, information, library, and knowledge management
In all, after restatement for loan hedges and the impact of DVA running, day 1 FVA, impact of Day 1 and change in CVA/DVA methodology, Corporate and investment banking delivered
This chapter is intended to support readers in the area of assistive living using wearable sensing, computer vision for lifelogging, human behaviour researchers aiming at
The national health priority areas are disease prevention, mitigation and control; health education, promotion, environmental health and nutrition; governance, coord-
The most common side effects include increased appetite, weight gain, increased blood sugar levels (especially if you have diabetes), gastrointestinal problems, frequent





