Syngress Hacking a Terror Network The Silent Threat of Covert Channels pdf
Full text
Figure


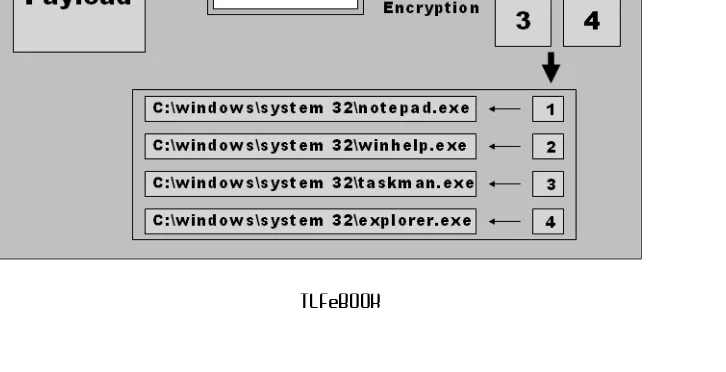

Related documents
Madeleine’s “belief” that she is Carlotta Valdez, her death and rebirth as Judy (and then Madeleine again) and Scottie’s mental rebirth after his breakdown.. All of these
Applications of Fourier transform ion cyclotron resonance (FT-ICR) and orbitrap based high resolution mass spectrometry in metabolomics and lipidomics. LC–MS-based holistic metabolic
• Follow up with your employer each reporting period to ensure your hours are reported on a regular basis?. • Discuss your progress with
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
information to reap an unfair benefit. Many of these donations were made at a time when it would have been illegal to make a sale of the same securities due to their access to this
To extend the program services to additional students and increase the sample for the research study, in 2014 Inwood House expanded the pool of schools further to include small,
4.1 The Select Committee is asked to consider the proposed development of the Customer Service Function, the recommended service delivery option and the investment required8. It
