Foundations of Security What Every Programmer Needs to Know pdf
Full text
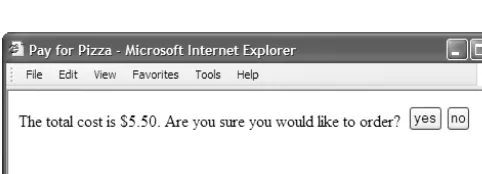
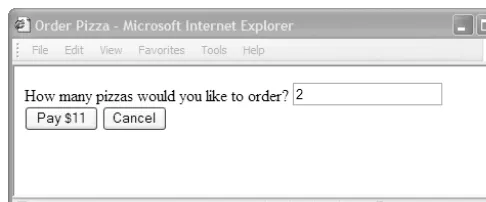
Figure
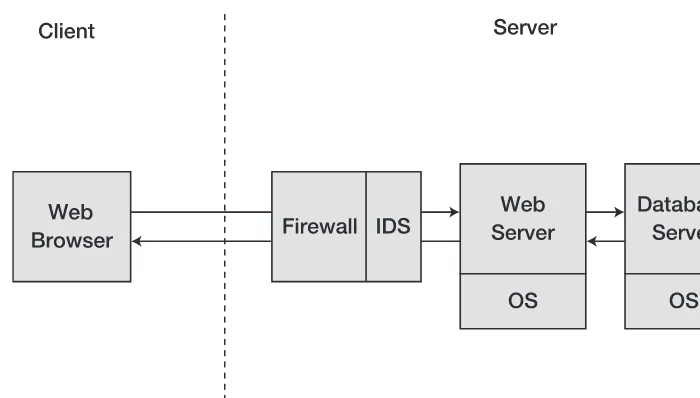

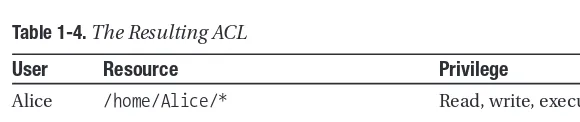
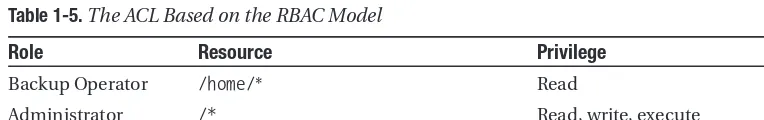
Related documents
Appendix A shows that the SST and atmospheric interannual variability (vorticity, shear, tropospheric moisture...) has a greater impact on TC activity than oceanic
One of the fastest-growing segments of Pentecostalism is churches that teach the Prosperity Gospel or, more disparagingly, “health and wealth.” Inspired by Oral Roberts, Kenneth
Dengan metode ini, foto yang sudah di-learning akan dicocokkan dengan hasil deteksi dari streaming kamera dimana pada streaming nantinya beberapa gambar dalam database
Clinical Resources in All Rural Hospitals for ACS
Indeed, adoption and application of a learning design taxonomy can provide a mechanism by which evaluation of many different significant and interesting approaches to
Mexico experienced the largest increase in UHNW wealth of US$15 billion in Latin America despite the US$9 billion decline in net worth of Carlos Slim, the country’s
The ten topics covered include the lifelong importance of health determinants in early childhood, and the effects of poverty, drugs, working conditions, unemployment, social
Control: With the help of CodeProfiler, Linde can ensure highest quality standards when cooperating with external ABAP developers. Governance: CodeProfiler provides