Detecting Malicious Web Scraping Activity: a Study with Diverse Detectors
Full text
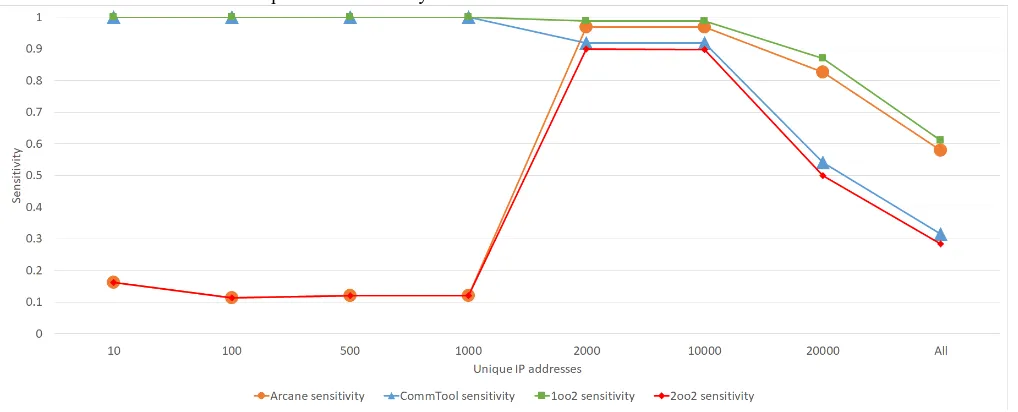
Figure




Related documents
"OISD hereby expressly disclaims any liability or responsibility for loss or damage resulting from use of the OISD Standards/ Guidelines/ Recommended Practices.".. a)
‘I thought “here goes” and we’ll just leave it at that … I should have, but I thought they might make you go onto another thing that costs more.’ This borrower said that
1) Threat modeling activity which refers to identify possible threats that can attack the software, so that appropriate security feature must take into
The focus of this research study is to ascertain teacher and principal perceptions of the overall effectiveness of School-Wide Positive Behavior Intervention Supports (SWPBIS)
With the assumption that TOA is the integer multiples of chip duration, our decoupled multiuser ranging (DEMR) estimator employs integrate-and-dump filter (IDF) in chip sampling
Subspecialties in radiology are officially recognised in less than 50 % of the countries and subspecialty training starts at a variable level of the training programme. There
California Childhood Obesity Conference: Protecting the Future of Our Children California Department of Health Services, the California Department of Education, the
ÜLKER BİSKÜVİ SANAYİ A.Ş.. is to manufacture of all foodstuffs and particularly, manufacture, purchase, sale, export and import of all kinds of flour and sugar,