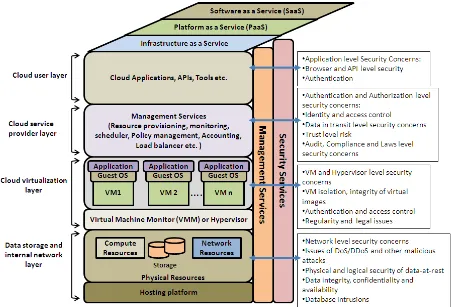
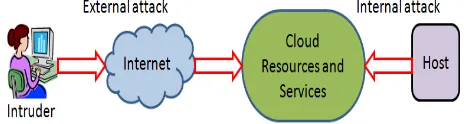
A survey on security issues and solutions at different layers of Cloud computing
Full text
Figure
Related documents
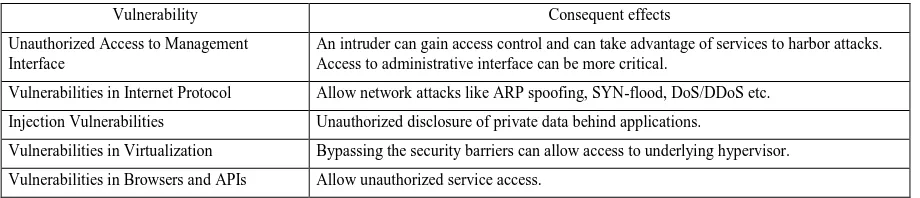
"Securit y Issues and Security Algorith ms in Cloud Comput ing",[20 12] Security Concerns:- Data, Access, Data Classification and Service Level Agreement
Cloud computing is a model for enabling convenient, on-demand network access to a shared pool of configurable computing resources (eg networks, servers, storage,
Security, Data Center Operations, Incident Response, Application Security, Encryption, IAM,
In particular we are concerned with the BPO-CCP's virtualization security, cloud data security, access control, user authentication and authorization, and
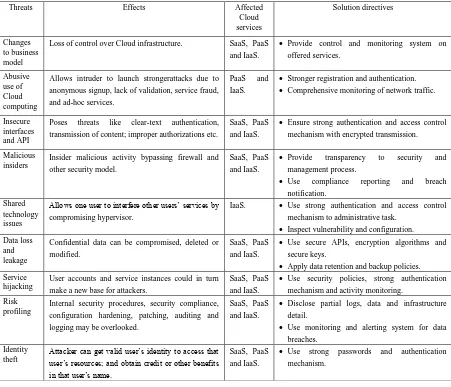
Cloud computing is based on a business model in which resources are shared (i.e., multiple users use the same resource) at the network level, host level, and application
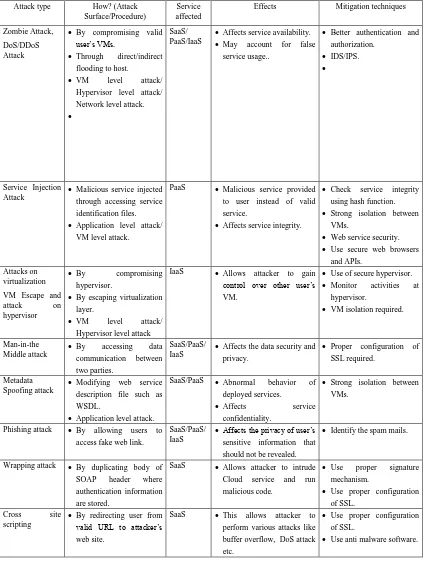
In this paper, we focus on security issues specific to cloud computing arising from computation outsourcing, multi-tenancy, remote network access, cloud
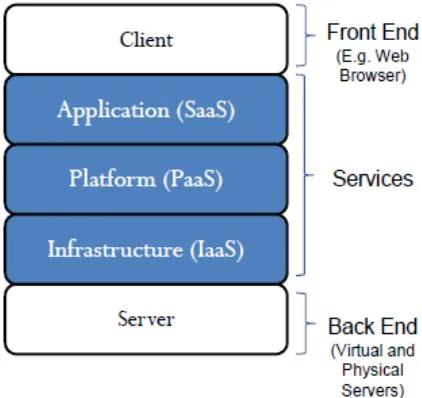
Storage Network Hardware Virtualization Infrastructure Platform Application... Speed
The rapid adoption of cloud computing services has been impacted by concerns over data security, data access, network latency, service levels, provider lock-in, and
![Fig. 6. Block diagram of cooperative agent based approach [28]. This approach is suitable for preventing Cloud system from single point of failure caused by DDoS attack](https://thumb-us.123doks.com/thumbv2/123dok_us/1551665.107719/16.595.169.417.144.294/diagram-cooperative-approach-approach-suitable-preventing-failure-caused.webp)
![Fig. 8. Securing virtual image repository and access control [37].](https://thumb-us.123doks.com/thumbv2/123dok_us/1551665.107719/19.595.151.458.393.568/fig-securing-virtual-image-repository-access-control.webp)
![Fig. 9.(a)Dual signature procedure (b) Service verification [40].](https://thumb-us.123doks.com/thumbv2/123dok_us/1551665.107719/21.595.99.499.487.632/fig-dual-signature-procedure-b-service-verification.webp)
![Fig. 10. Re-encryption based approach [41].](https://thumb-us.123doks.com/thumbv2/123dok_us/1551665.107719/22.595.162.471.208.419/fig-re-encryption-based-approach.webp)