A Secure Boot Loader System for Loading an Operating System with Fingerprint Authentication
Full text
Figure
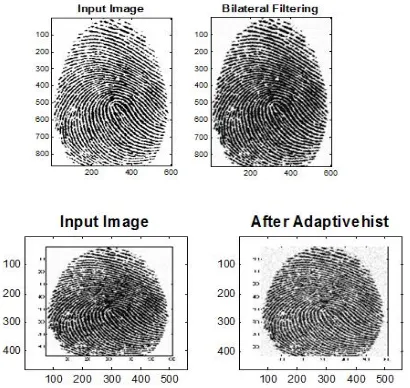
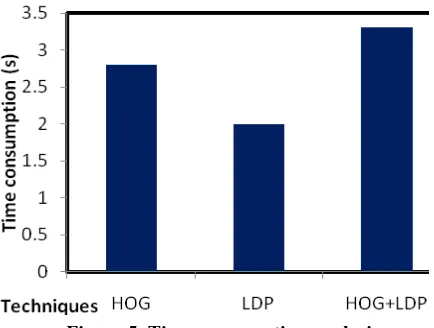
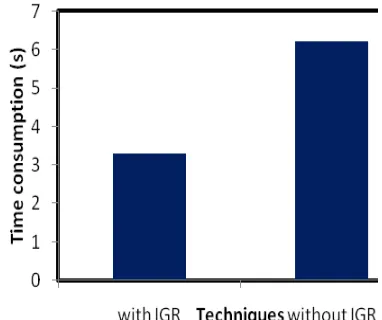
Related documents
In the recent years, high priority has been given towards systematizing and scoping the e-Participation field, addressing research gaps, and driving future research directions
The purpose of this research is to determine the issues of the performance of current encryption methods in AES-CCMP in different types of devices and handle it so
We recommend that is used the cognitive behavioral intervention as a strategy to improve the disabled professional basketball players’ profile of mood states
They would not only become aware of their own inner strengths and characteristics (Seligman et al., 2009), but they would also feel the use of true partnership of the family
response Total defoliation [%] Percentage of secondary shoots [%] Resistant tree ≤ 35% - slightly damaged tree ≤ 50% - slightly transformed tree Resilient tree ≤ 35% - slightly
parental background (social class, economic and cultural capital) on the choice of subject in.. secondary and higher education in
(2012) looked at how the components of the AMOC changed during a warming scenario in a model sim- ulation and found that the reduction of the AMOC was pri- marily a reduction
[15] In 2009, the radiographs of two different groups of Turkish dental patients were examined for the prevalence of pulp chamber calcification and were reported to