Wi Fi Security pdf
Full text
Figure
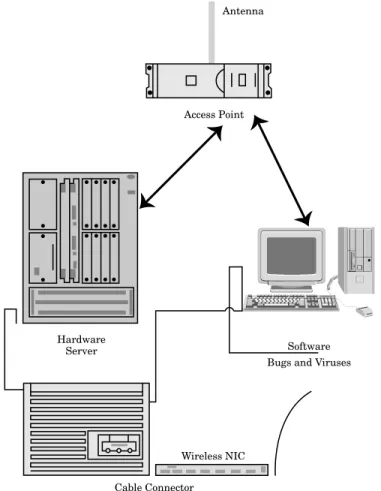
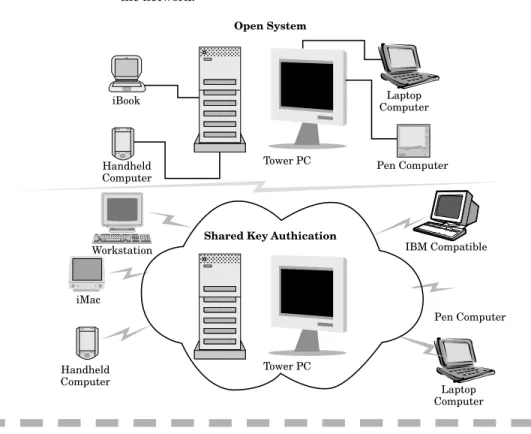
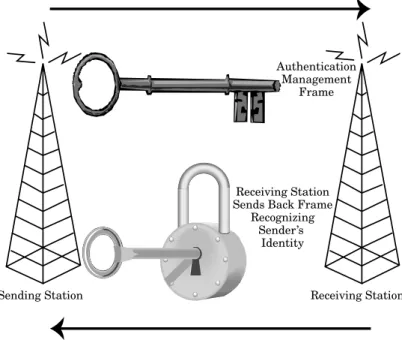
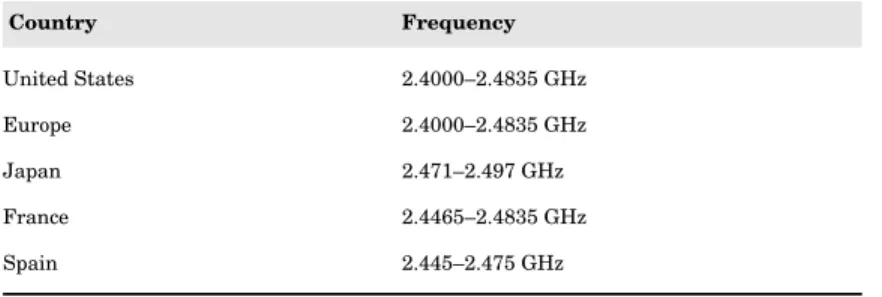
Related documents
If the WAP is not issued an IP address on the network, or needs to be accessed while not connected to a network, you can configure your computer's network connection to allow
A Cloud based Wi-Fi Management solution with Intelligent Wi-Fi Access Points allows instant and remote configuration of each Wireless Access Point, where IT does not have
The camcorder can connect to a Wi-Fi network using a wireless router (access point) and even remember the settings for the 4 most recently used access
Place the SA-4 amplifier so that the wireless adapter is within range of your Wi-Fi ® router or network access point.. • Place the SA-4 amplifier and wireless adapter in an
The application DOES MEET the statutory requirements for the Population based Methodology for issuance of a Permit of Approval to construct a new seventy (70) bed nursing home
The Avaya 3616 and 3626 Wireless Telephones leverage the IP Office Wi-Fi data infrastructure—there can be up to 6 wireless phones per access
Plugging a wireless access point into the Optional port increases the security of your mobile wireless computers by creating an IPSec VPN tunnel from the wireless computer to
On Windows XP SP2 and later, Firewall support is provided by Windows Firewall. Unlike earlier versions, Windows XP SP2 can be used on a system that you intend to use as a UPnP
