Oracle Linux Security Guide pdf
Full text
Figure
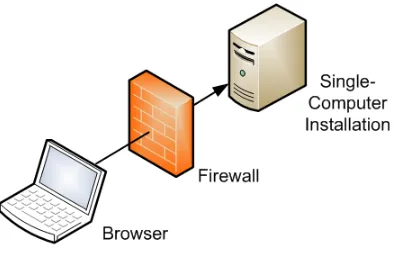
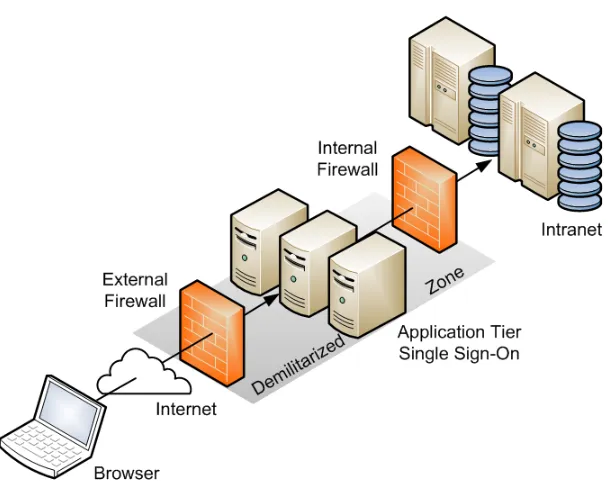
Outline
Related documents
The case of Neo (the protagonist of The Matrix trilogy) is, I believe, significantly different as far as the objectives of this essay are concerned. At the beginning of
As well as their integration into the bespoke 3D virtual environment, the dialogues were therefore also enriched by adding an interpreting brief to each of them and
In a health care context, remote measurement technologies (RMT) can be used by health care professionals (HCPs) and clinical teams to collect data on a patient’s
The goal of this lesson will be to help students understand the plot of Macbeth and accustom them to the language and issues that develop from this text.. Also, looking at this
stages in the liver will remain a challenge for the PNG National Malaria Control Programs as the low dose PQ treatment recommended in the absence of G6PD testing is unlikely to
While the results reported in Table 3 indicate that these seven variables are more or less equally associated with the assessment of truthful versus untruthful statements, it
Whether it’s a smartphone app, or a browser-based solution that can be accessed via a mobile device, employees need to be able to access their schedules, request time off, and
The comparison was performed with single runs and simulated data of different available con figurations of CAN- ARY (González-Gutiérrez et al. 2018 ) and, consequently by