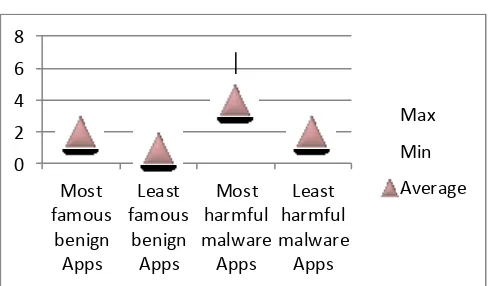
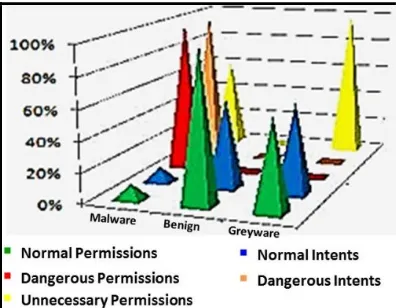
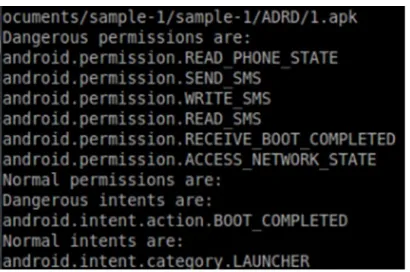
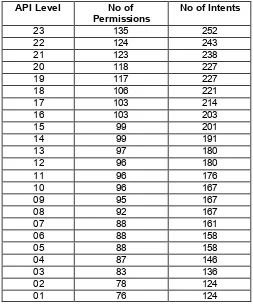
Investigating Android permissions and intents for malware detection
Full text
Figure



Related documents
Figure 4.1: Comparison of running time of K-means algorithm on five different inds of platforms (including single core machine) with varying number of clusters k and number of
An Analogy Information Warfare Field Agents HQ Analysts Decision Makers.. Framework Framework Data Collection Data Storage Data Decision
Current Family and Significant Relationships (See Personal History Form) Strengths/support:.. Stressors/problems: Recent changes:
Downtime Analysis of Tube Filling and Carton Packing Machine at FMCG Company1. Paragjyoti Baishya 1 , Ajoy Krishna
index closely matches the swings in inventory change and hence is a leading indicator of business cycles; the PMI-all index matches every business cycle with an
Average (period 1994–98) annual age-standardized incidence and mortality rates of invasive ovarian cancer for individual Canadian provinces, for Canada and for the United
Treat fruit with an appropriate chemical from the Problem solver handy guide.... White eggs around
Whereas in developing countries, such as Saudi Arabia there is a lack or nonexistence of Child Nutrition Programs collaborated with public or private schools to provide