Agent-based (BDI) modeling for automation of penetration testing
Full text
Figure
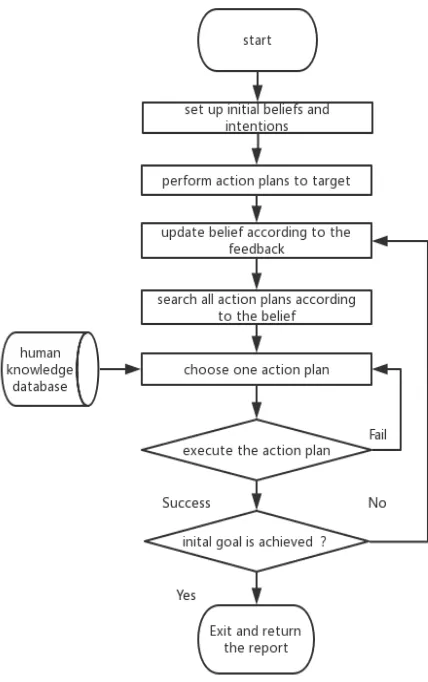
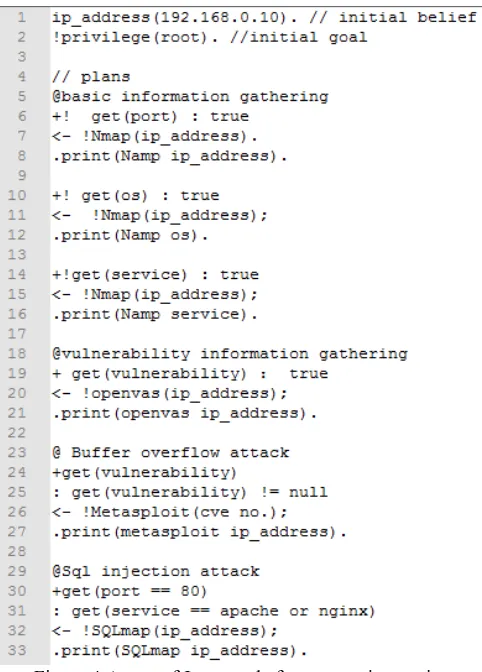
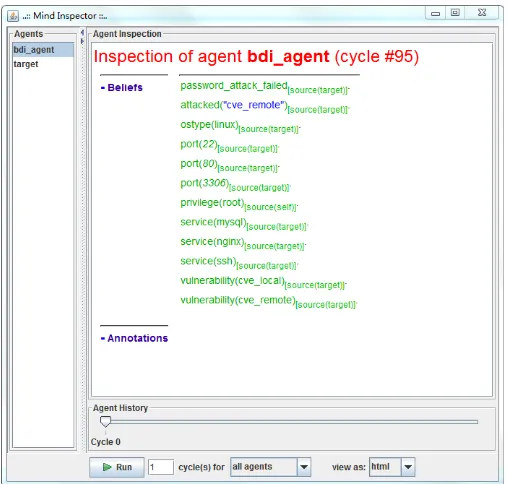
Related documents
Like relationship marketing, the costs of customer acquisition and desirability of customer retention are key features of CRM (Roberts, 2000; Zeithaml, 2000). However,
We also see that using the features from the ProsoTool algorithm did increase the performance of the classifier, leading to a relative error rate reduction of more than 24% compared
Although the SCPDF did not use the professional standards as a framework, the SCPDF used a technology focus to encourage teachers to improve their practice of using technology
The research is designed using the Action Research Model in three phases. Phase I: Pre-ODI where the two groups, one with overseas experience and the other non-overseas
Prior research published in Technological Forecasting and Social Change has explored various aspects of ACAP: Ranguc and Slevec (2017) examined the impact of ACAP on manufacturing
levels governments (institutional factor), high transportation costs (infrastructural factor), and difficulties in obtaining a loan (access to finance factor). Some
This includes the challenge networks, module identification method descriptions and code provided by teams, the final module predictions of all teams for both sub-challenges,