Perfect Passwords Selection, Protection, Authentication pdf
Full text
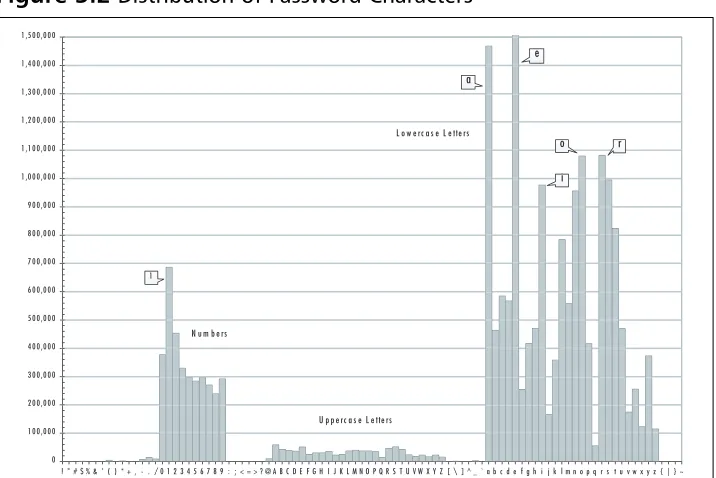
Figure



Related documents
Page Yield: When comparing the total pages printed from all cartridges tested, it was concluded that overall Original HP inkjet print cartridges produced 209% more pages than
trapdoor and use it to learn all future emails with that category. One can assume that the server cannot memorize trapdoors but this is a very restrictive assumption and not easy
The provisions of an international convention on licensing, authorisation, selection and training of private military and security personnel would contribute to the establishment
Such a collegiate cul- ture, like honors cultures everywhere, is best achieved by open and trusting relationships of the students with each other and the instructor, discussions
(2001) which has attempted to value the finance and insurance roles of cattle based on the costs saved, by considering costs of alternative ways of financing or insurance other
Van Baals beleving van het Mysterie komt duidelijk in beeld door de donkere velden in zijn benadering: de beleving van de conti- nuïteit van de groep, de dialectiek met de omgeving
Additional penalties apply for failure to submit transfer pricing documentation: a minimum penalty of 10,000 euros (approximately US$13,600) or up to 5 percent of the gross
The articles of this special issue on cognitive load theory discuss new conceptualizations of the different categories of cognitive load, an integrated research perspective