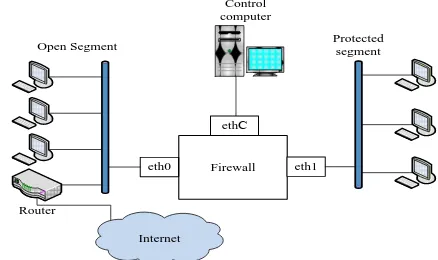
Methods for Applying of Scheme of Packet Filtering Rules
Full text
Figure


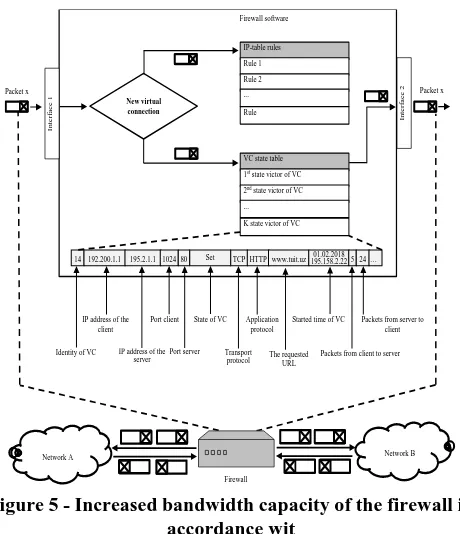
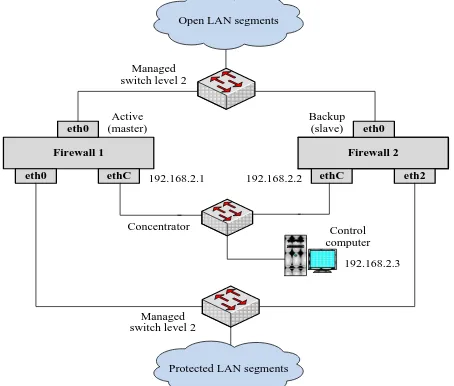
Related documents
Skeletor, injured badly from the fall, picks up his Sword of Darkness from the ground and raises it in the air. SKELETOR
• The Medicaid cost report captures the actual costs of providing Medicaid covered health-related services as reported by the LEAs, which will be compared to Medicaid
The CAA 507 Programs consist of three parts: a Small Business Ombudsman (SBO) to act as an advocate for small business, a Small Business Environmental Assistance Program (SBEAP)
# iptables -A INPUT -p tcp --dport 22 -j ACCEPT + Allow inbound web connection:. # iptables -A INPUT -p tcp --dport 80 -j ACCEPT + Set default policy for all other connections:
The authors have explored an integrative framework for knowledge management in support of ERP (Enterprise Resource Planning) systems implementation.. The framework
Soldiers with CDH used abortive headache medications an average of 15.1 days per month compared to 3.3 days per month for soldiers with episodic headache (P < .0001)..
These strategies have the potential to improve retrieval of information when needed for use as a source for problem-solving (Boudreaux, 2010). Furthermore, all
The nature of the work performed in small businesses within higher knowledge-intensity sectors (in our study, software companies) required higher level of use of information