A Trust based Multipath Routing for Black Hole Attacks with Group Search Optimization Routing
Full text
Figure
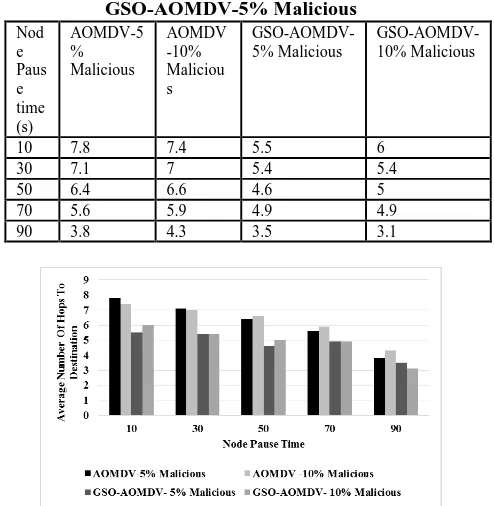
Related documents
The sensor nodes within two hops operate in multi-hop mode as they transmit data, and the remaining nodes operate in virtual MIMO of SISO mode. An algorithm for determining
Ad hoc On demand Distance Vector (AODV) is one of the most suitable routing protocol for the MANETs and it is more vulnerable to black hole attack by the malicious nodes.. In
Rats pretreated with PJ either with high or low doses showed a signi fi cant reduction in the copper content in liver tissues by 30% and 56% in rats pretreated with 1 and 3 mL/kg
At the present time, according to the DSM-IV-TR 16 , in order to diagnose paedophilia it is necessary that, over a period of at least 6 months, the person presents
Sriplang K, Adisakwattana S, Rungsipipat A, Yibchok-Anun S., Effects of Orthosiphon stamineus aqueous extract on plasma glucose concentration and lipid profile in
Percent changes in intake of dietary components, Healthy Diet Score and Dietary Inflammatory Index were calculated and related to body mass index (BMI), serum cholesterol
microscopy tasks into an undergraduate pathology course in an attempt to render the instruction more process- oriented. The research questions were: 1) How is virtual
OYAK ANKER BANK GMBH GERMANY 2231 227. OYAK