Detection and Elimination of Black Hole Attack in WSN
Full text
Figure

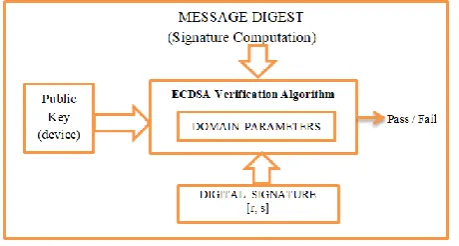


Related documents
A large number of other integrals involving spheroidal and modified Mathieu functions can also be obtained from (2.1) and (2.5) on account of the most general nature of
Stochastic ground motion simulations for the 2016 Kumamoto, Japan, earthquake Zhang et al Earth, Planets and Space (2016) 68 184 DOI 10 1186/s40623 016 0565 3 F U L L PA P E R
Equation 2 also shows that a new inversion that spans just a small number of loci involved in local adaptation will not spread if it carries any immigrant alleles.. Spe-
The Figure 1.a represents the SEM micrograph of pure PPy. The figure represents the size and spherical nature of PPy particles. The SEM micrograph is shown a characteristic peak
International Journal of Scientific Research in Computer Science, Engineering and Information Technology CSEIT1833369 | Received 20 March 2018 | Accepted 31 March 2018 | March April 2018
(2002) Binding of the natural killer cell inhibitory receptor Ly49A to its major histocompatibility complex class I ligand. Crucial contacts include both H-2Dd AND
Klason lignin and sugar content of the wild type group and the different genetic lines of transgenic aspen subjected to different decay treatments.. Syringyl to guaiacyl lignin
Tygar, 2010 : Machine learning advocates have projected learning-based systems for variability of security applications, containing spam detection and network