Model driven certification of Cloud service security based on continuous monitoring
Full text
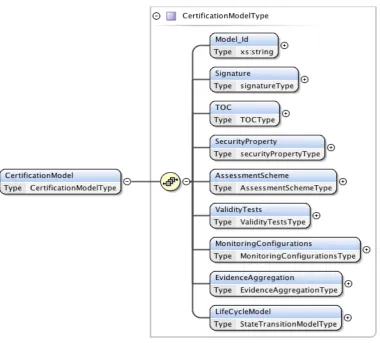
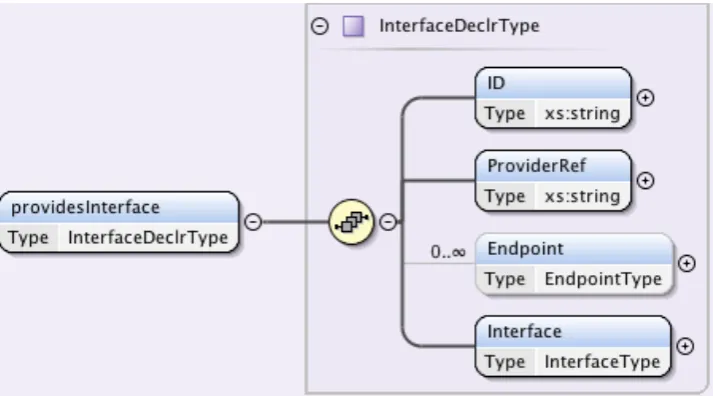
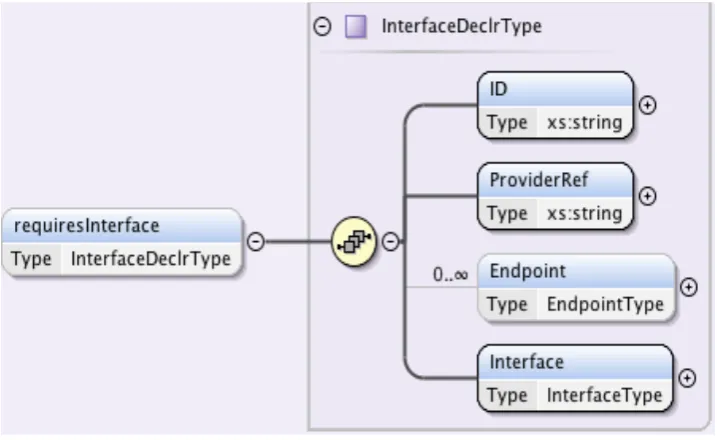
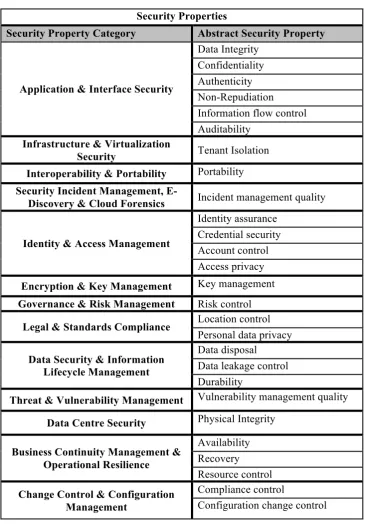
Figure
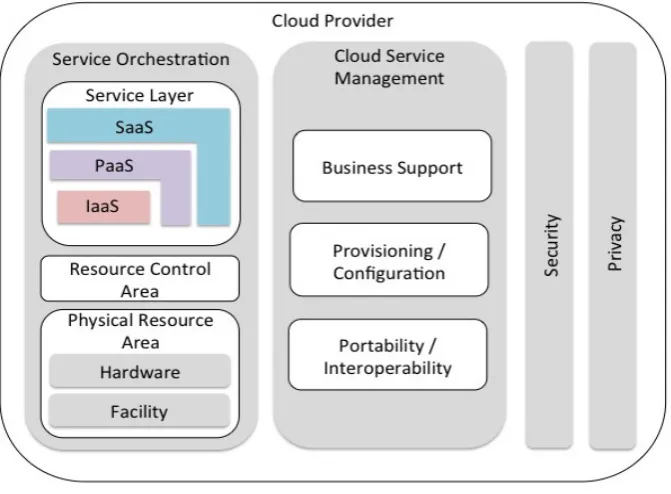
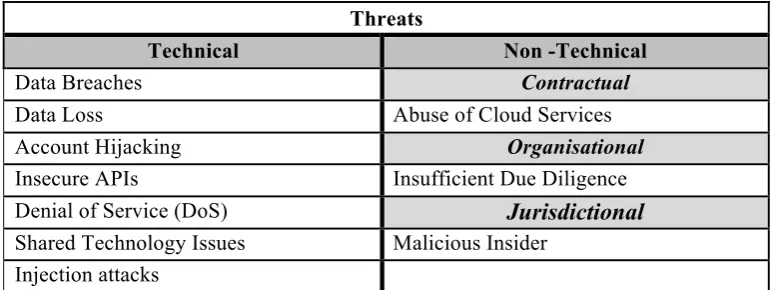
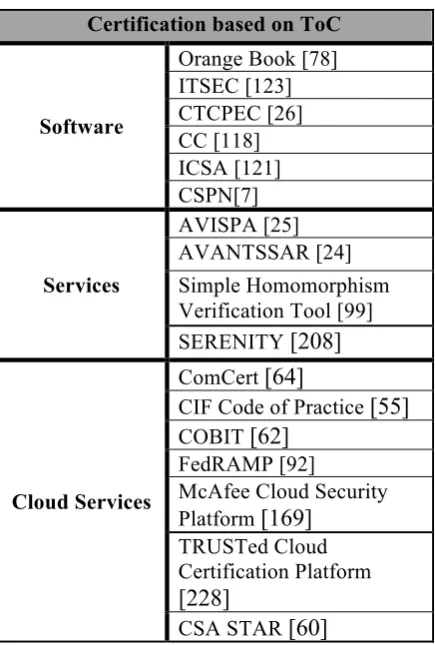
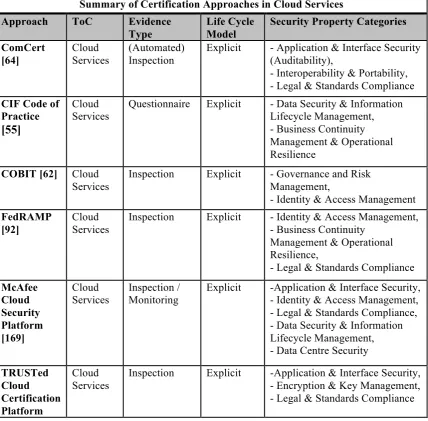
Outline
Related documents
• Demonstrate feasibility of using mobile data to identify potential savers • Provide banks with a new way to qualify and contact new market segment • Extract lessons for other
In a military staff setting, Ohlsson, Hedlund, and Larsson (2016) examined the relationship between personality dimensions, political skills and team performance, link- ing
The increased connectivity between the TRN and PFC under ketamine treatment suggests that the influence of the TRN on PFC activity becomes greater in ketamine
You can take advantage of the digital audio output from your set-top by connecting a suitable cable between your home theater receiver and the OPTICAL AUDIO OUT connector (as shown
Note: ACTIVE command is generated by dummy memory read from address 0 when FT800 is in sleep or standby mode.. This is followed by 2
10 crores or more and experience of minimum three years or more to establish and operate computerised ticketing system on contractual basis at the National
DEM Democratic REP Republican UND Undeclared UNK Unknown.. If no selection is displayed, everything
Non-literary texts are chosen from a variety of sources and media to represent as wide a range of text types as possible, and works are chosen from a variety of literary forms..
![Figure 3 – EVEREST Architecture (Source [218])](https://thumb-us.123doks.com/thumbv2/123dok_us/1452132.97797/75.595.92.492.176.417/figure-everest-architecture-source.webp)