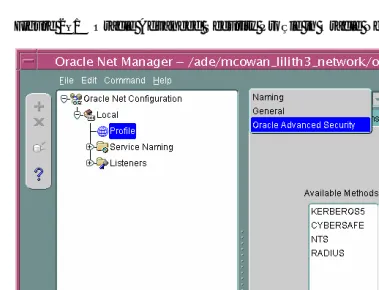
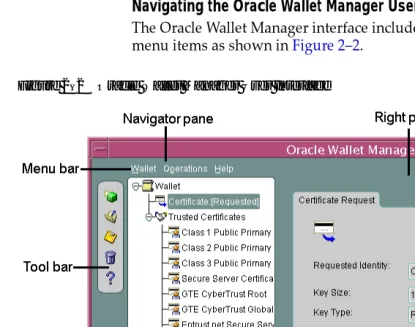
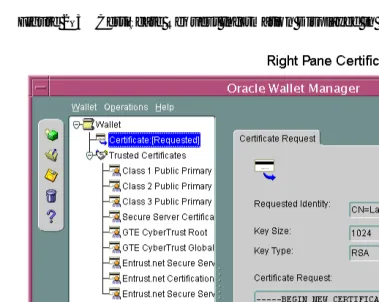
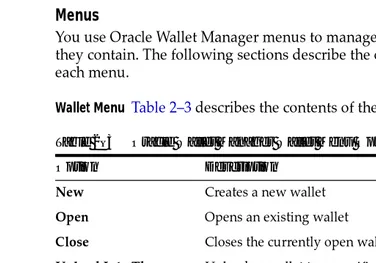
132 Oracle 10g Advanced Security Administrartors Guide Ww [ PUNISHER ] pdf
Full text
Figure
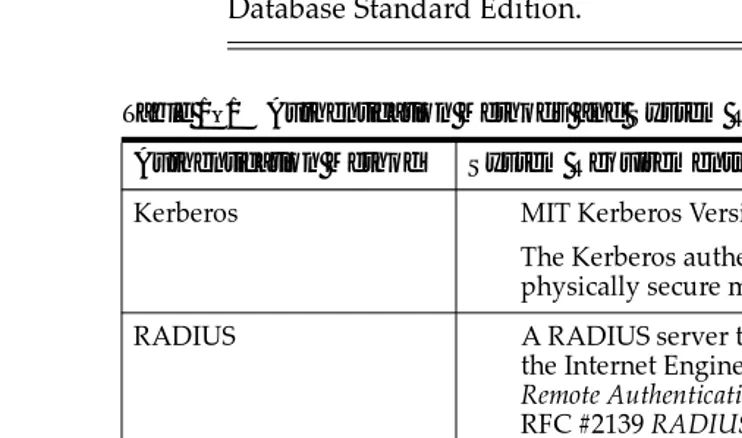
Related documents
Guided tissue regeneration in intrabony periodontal defects following treatment with two bioabsorbable membranes in combination with bovine bone mineral graft. The
We developed ‘Positive About Borderline’ for mental health nursing staff. It is a 1- day BPD-related training programme comprising two key elements: i) ‘The science of
building control systems and operational log feeds to support the iterative and increasingly accurate modelling of energy efficiency-related behaviour through correlation and
The next step in estimating adult productivity benefits is to link the impact of various Latin American and Caribbean early child- hood programs on childhood cognitive skills
The directory entry gives in general an overview of the different components of the stored geometry and it points to records in the Parameter Data section which contains the
An individually rational separating contract, on the other hand, will induce investigation if and only if information about the ex-ante type is sufficiently valuable for the agent
Mackey brings the center a laparoscopic approach to liver and pancreas surgery not available at most area hospitals.. JOSHUA FORMAN, MD
From a Korean perspective AustranaTs it eleventh largest export market and sixth most important import sour~ While Korea's financial and economIc cnS1S of 1997-98