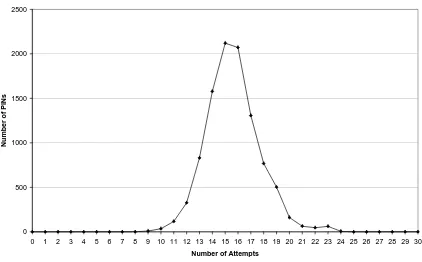
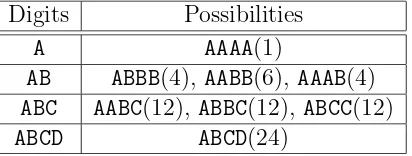
Credit Card Visa Hack pdf
Full text
Figure



Related documents
Second, the Commission should provide targeted, time-limited funding from USF (with the amount and distribution to be evaluated periodically) for digital literacy training in schools
In effect, the robust rules acknowledge the uncertainty in the estimated model, and thus trade less aggressively than the nonrobust rule, and this improves out-of-sample
The clustering rate is typically much faster and the maximum memory requirement is considerably lower, but the heuristic algorithms do not work as accurately as the best
facility — first international Stocking and Service Center — and secured first international Partnership Program customer.. Moved headquarters to new offices in
Figure 87 Optical microscopy image of TiAl alloy powder ... 114 Figure 88: Particle size distribution of the different TiAl alloys powders. 117 Figure 91: Powder sampling
Through a landslide inventory and morphometric analysis of the subaqueous slope failures at the coastal areas of the populated distal basin of Lago Nahuel Huapi (where the 1960
In this paper, an efficient and new numerical method is proposed for the numerical solution of singular initial value problems, which is based on collocation points with
The landscape plan shall be subject to review and approval by Gwinnett County Department of Transportation and the Director of Planning and Development.. Provide