Hacking attacks and Examples Test pdf
Full text
Figure
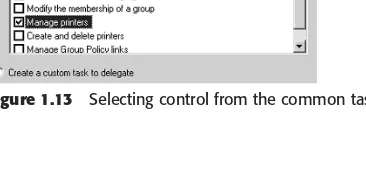
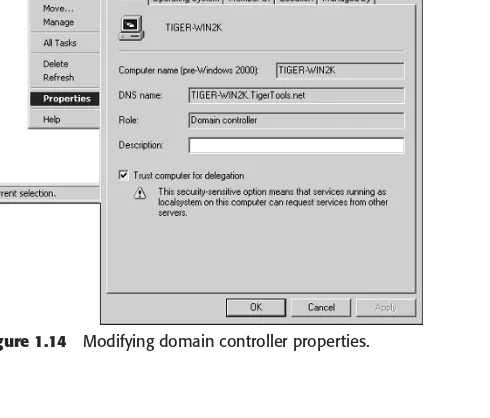
Outline
Related documents
Pure Java Windows authentication supports connections to Microsoft SQL Server 2000 and Microsoft SQL Server 2000 Enterprise Edition (64-bit) SP2 or higher in a Windows domain
I want to better explain the motivations and barriers to physical activity and exercise for university students at the University of South Florida (USF) Department of
EXCELLENCE EXPERTISE INNOVATION Tuberculosis Infection Prevention in Health Care Settings Jeffrey L.. Levin,
If Active Directory is installed on a Domain Controller running Windows 2000 Server (or higher), and the client browser supports the Kerberos authentication protocol, Kerberos
Daily soil moisture measurements from the Automated Weather Data Network (AWDN) station located adjacent to the (a) subirrigated meadow, from the Bowen ratio energy balance
The College of Engineering also embraces the goals of fostering teaching, scholarship and outreach on an interdisciplinary basis. The certificate program will support
cent of patients reported that they experienced consti- pation despite taking laxatives, and more than half said that constipation had a “moderate-to-great” or “great” impact on