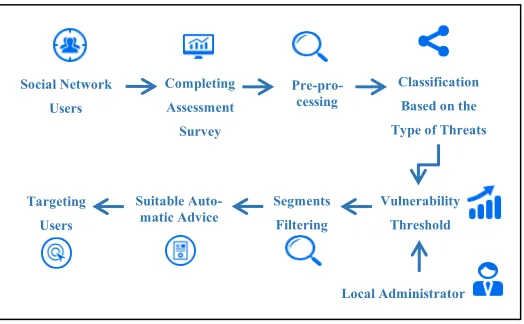
A semi-automated security advisory system to resist cyber-attack in social networks
Full text
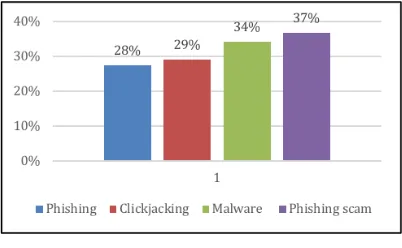
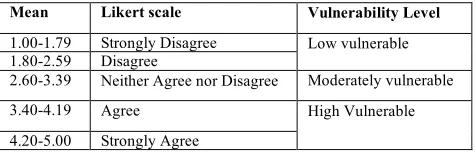
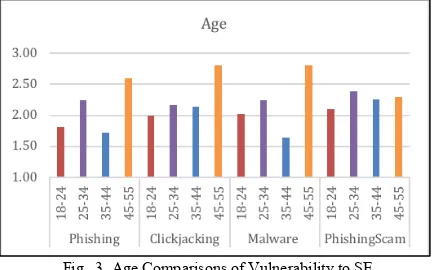
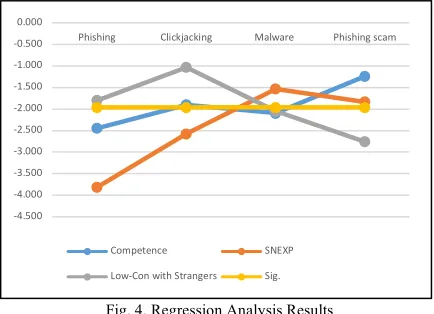
Figure
Related documents
Denna handling får ej delges annan, kopieras i sin helhet eller delar utan vårt medgivande. Överträdelse härav beivras med stöd av
According to the qawmi madrasa ulema , individuals, irrespective of their social standing, continuously re-produce correct religious tradition based on the knowledge and
The current study used polynomial regression and response surface methods to explore the relationship between agreement and disagreement between student-ratings and teacher-ratings of
From the above analysis it is clear that after the merger we can see that in various financial parameter of the bank performance have improved in both cases and the success of merger
mechanisms.” 1 The Certification and Accreditation (C&A) process is the primary mechanism to ensure that baseline security controls are applied and additional controls
To this end we propose a Conceptual Graphs [13] based language, Layered Conceptual Graphs [6] for representing the interdependencies amongst policy rules.. The visual, logic
(a) Civil service reform, corporatization, privatization, establishing clearer objectives for public institutions, restructuring such institutions to achieve greater focus
We will show that the simple polarized incoherent phase observed in Ref.(25) can be captured by perturbation theory and show that its excited states can be reproduced by