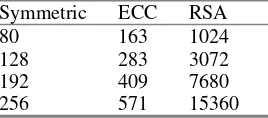
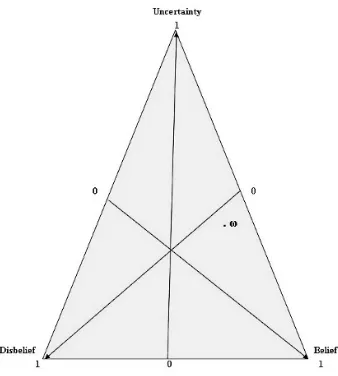
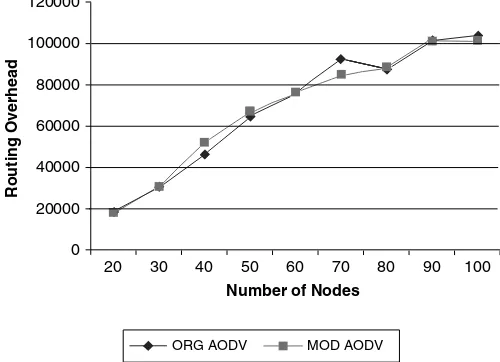
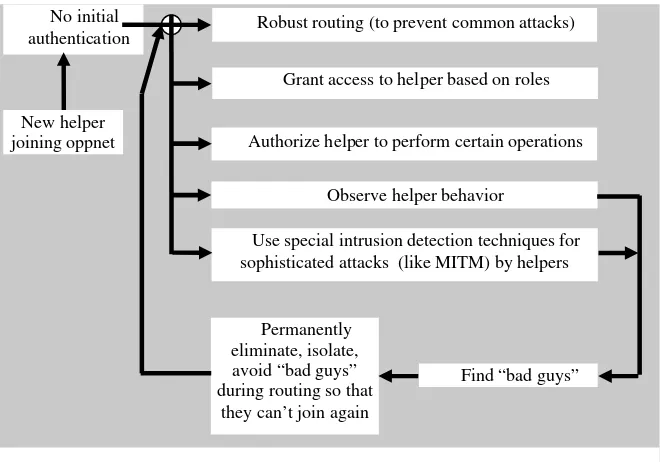
Mobile & Wireless Network Security & Privacy pdf
Full text
Figure
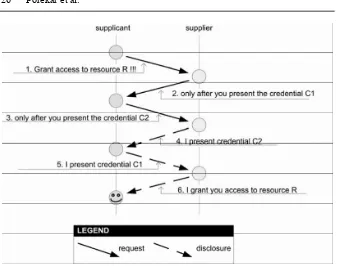
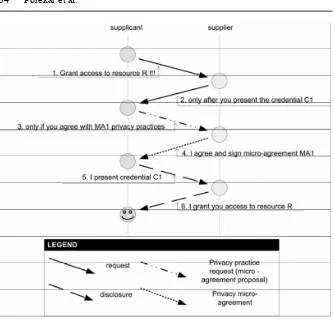


Related documents
Agreeing to use a particular forum means waiving certain legal rights. In a permissive agreement, the parties waive their objections to litigating in a particular court.
In addition to learning the “low-cost” methodology to energy auditing at the Energy Audit Institute, graduates are equipped with software to calculate energy savings, and
The electrochemical properties were studied using cyclic voltammetry (CV), galvanostatic charge-discharge techniques, and electrochemical impedance spectroscopy where
If you do choose to have your information shared, in an effort to protect you, third parties who have access to personally identifiable information must abide by the current
Hire and manage information systems personnel and contractors to design, develop, implement, operate and administer computer and telecommunications software, networks and
While Malaysia is boosting the national economy with development palm oil industry, the palm oil industries in Malaysia are generating large quantity of oil palm byproducts during
Information technology equipment (ITE) Racks and cabinets Cabling pathways (not shown) Building steel Supplemental bonding grid (SBG) Conduits Rack bonding conductor
Engineered to best analyze gaze on a plane (e.g., a retail shelf), both portable eye-tracking glasses and computer monitor–mounted hardware can play key roles in analyzing