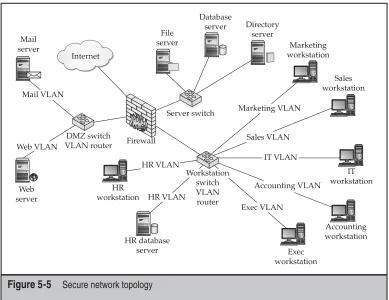
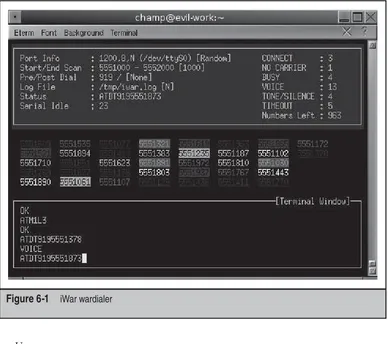
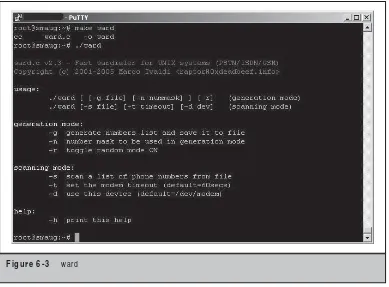
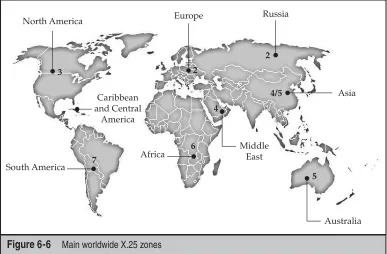
Hacking Exposed Linux Linux Security Secrets & Solutions, 3rd Ed pdf
Full text
Figure
Related documents
Based on our information, no numerical study has been carried out yet on the conjugate heat transfer of the nanouid ow in double-pipe heat exchangers that considers the mutual eects
It analyzes which types of financial and non-financial institutions report their remittance transactions to central banks or other financial sector authorities, what types
to be invested in company shares, and the Trust Agreement contains language that seems to give the fiduciaries some flexibility in offering company stock’’ (citations and
Vandenberghe Remi X Vandenbroucke Simonne. Vandenberghe Remi fs, Vandenberghe
When information about nationality was available, accent strength primarily affected natives’ impressions of speakers from high status countries: in both Study 2 and Study 3,
DMACC Iowa Culinary Institute (ICI) first-year students Jennifer Shadow (left) of Waterloo and Randall Brown of Urbandale finished in first place in the recent Taste of Elegance
AUC-L: Average area below the target range; avg.: Average; CGM: Continuous Glucose Monitoring; CGM-GUIDE: Continuous Glucose Monitoring-Graphical User Interface for Diabetes
Lawyers and law school clinics have become myopic in their approach to civil domestic violence lawyering. This article argues that domestic violence lawyering should