Professional Penetration Testing Creating and Operating a Formal Hacking Lab pdf
Full text
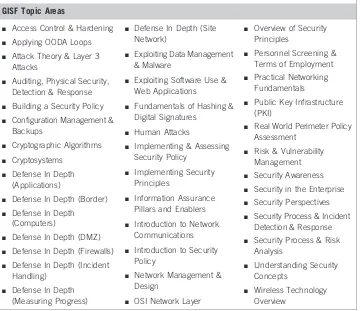
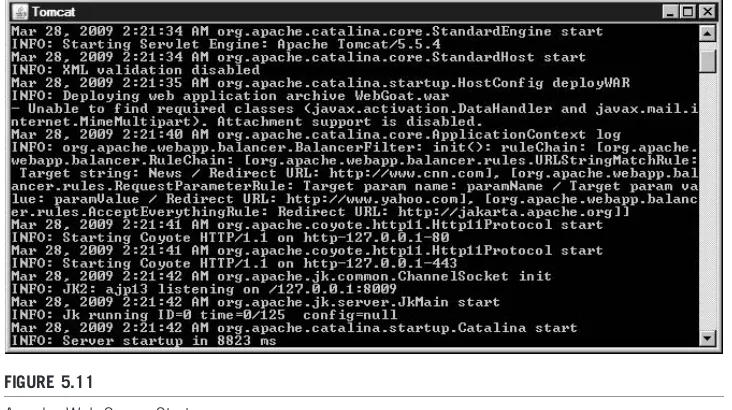
Figure

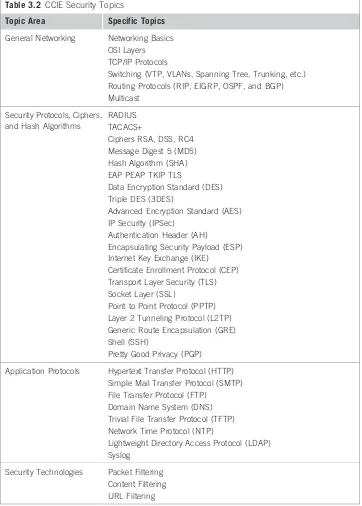
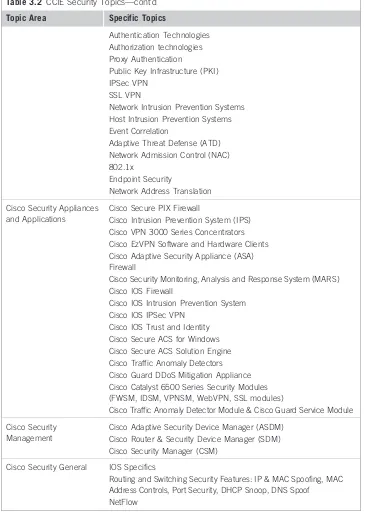
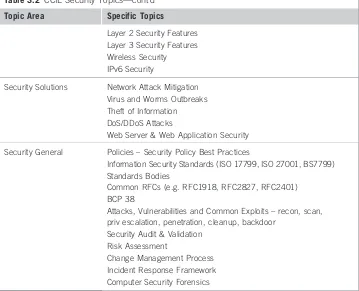
Related documents
Para la generación de dicha aplicación, se utilizó software libre y de código abierto, por medio del uso de la plataforma OpenGeo Suite 4.5; la suite utiliza
The findings in the present study support the impor- tance of assessing antenatal depressive symptomatology and monitoring Chinese women with significant antena- tal depressive
ng/ml) showed 3.5 fold increase in collahen synthesis and 2.5 fold increase in noncollagen synthesis*(p<0.05)... 이러한 사실은 실제 생체내에서 적용하기에는
We have chosen to create a Decision Support System (DSS) to help users write their complex policies [19]. DSS are a set of methods and techniques used to help someone
City-wide PM City Scorecards Outcomes, indices Surveys, benchmarking Organisational PM Departmental Scorecards Input, process, output Impact Audit Reports Individual PM
The Digital Privacy and Security Statement made by the Global Commission on Internet Governance (2015) was scrutinized with a cosmopolitan focus in order to prove its
By this stage of Achilles tendinopathy there are numerous changes that have occurred in the tendon which result in its physical structure being broken down and making
It is essential that people with both mental health and alcohol misuse problems are aware of and have access to local support services available, such as those offered by