Security metrics for the Android ecosystem
Full text
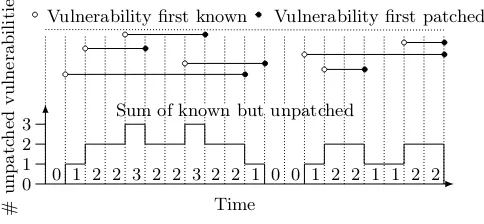
Figure


Related documents
Compared to the supervised results, the TFIDF approach is worse in terms of the individual maxi- mum F-measure, but achieves similar performance when using the weighted relative
A statistically significant negative correlation was dem- onstrated in the study cohort between the maternal serum PIGF levels, foetal heart rate (FHR), birth weight and length,
Options for the sewer alignment were developed and we consulted with Yarra and Boroondara councils, Parks Victoria, Vic Roads, Latrobe Golf Club and.. Wurundjeri.Tribe, the
The effect of the printing parameters (i.e.. rate and layer height) and the physical properties of the polymer (i.e. thermal transitions and rheological behaviour)
In view of the the nexus between literature, memory and identity in German culture, an exploration of these questions should not only illuminate the way in which Germans
● The majority of Mexican admissions reported that they first used their primary substance of abuse before the age of 18 (60.7 percent for males and 56.1 percent for
organisasjonslæring, arbeidsplasslæring, uformell og formell læring, læring gjennom praksis, sosial praksis og så videre vil derfor være nyttige når man skal foreta en studie