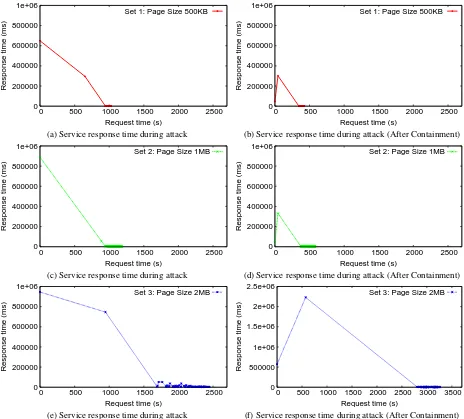
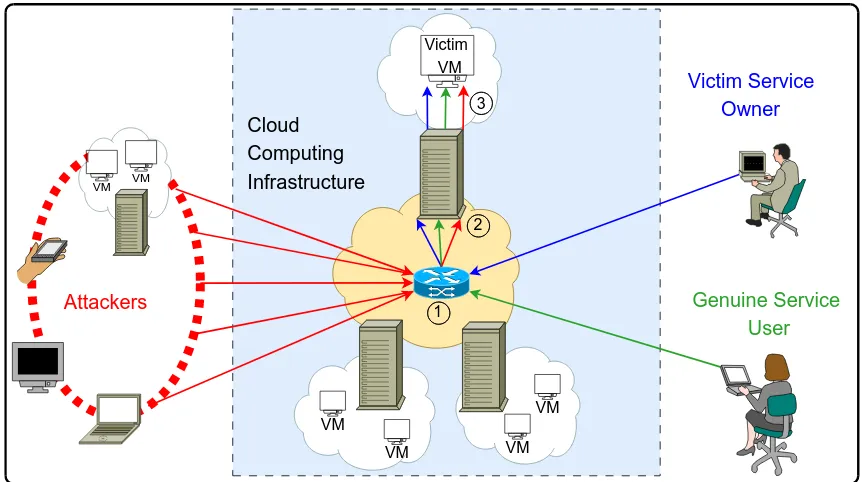
DDoS victim service containment to minimize the internal collateral damages in cloud computing
Full text
Figure



Related documents
The clear outcome of this research project is that a small wind turbine is an economically and technically feasible renewable energy generator that has the potential to
Benchmark - In the same way that an organization will consider their financial position by comparison with previous years, so the regular use of online surveys will allow an
Data source: Eurostat: labor force participation rate by gender, part-time employment, February 2013. Increase in female labor force participation rate in percentage
Traditional telecommunications facilities and data centers both rely on dc battery systems to provide interruption free power to critical equipment.. In the telecommunications
In the current literature, some papers study the new item forecasting (e.g., [ 60 – 64 ]), but very few papers explore the new item forecasting in fashion industry, and
interval [ 7 weeks between neoadjuvant therapy and surgery improves pathologic complete response and disease-free survival in patients with locally advanced rectal cancer. Ann
The aim of the analysis is finding the relation between the taxonomy of individual competences based on a selected EUCIP Elective profile (IS Manager) and IT
• The Relocating assembler has to provide object code and relocating and linking information to the Loader.. – Length of program