Building an Effective Intrusion Detection System using combined Signature and Anomaly Detection Techniques
Full text
Figure

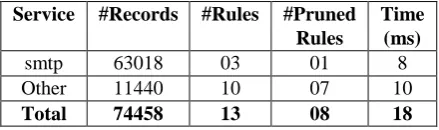

Related documents
Further- more, squamous cancers showed a higher tendency of bladder muscle invasion at diagnosis compared to non squamous cancers (p=0.00167), with no significant stat-
The MMASCS multi modal annotated synchronous corpus of audio, video, facial motion and tongue motion data of normal, fast and slow speech Dietmar Schabus1,2, Michael Pucher1, Phil
The distance measurement with the LIDAR is based on the indirect time‑of‑flight method using the relative ratio of the accumulated charges in capacitors connected to photodiode
On Wednesday, we have the bank of Canada policy announcement where we are expecting a removal of the language of a rate cut. This should prompt the $C to rally, thus hurting growth
Variabel bebas dalam penelitian ini adalah rasio Kinerja keuangan , Good corporate governance dan corporate social responsibility , dan yang menjadi variabel
Silvio Luigi Feliciani.. THE BACHELOR DEGREEE PROGRAM IN THE MUSIC THERAPY COURSE OF THE CONSERVATOIRE OF MUSIC IN
The aim of this study is to examine the relationship between assessed sensory modality preferences and athlete status, gender, and sport, using the VARK athlete questionnaire..