Secure and Access Control Data Monitoring in Vehicular Ad Hoc Network
Full text
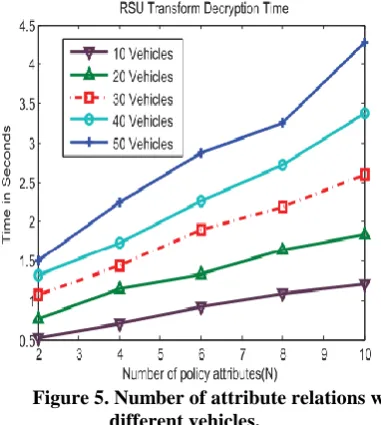
Figure


Related documents
Knowles; Chitre Vivek; Chloe Rochester; Chris Coldwell; Chris Dawson; Chris Homer; Chris Lewis; Chris Nutt; Chris Thorn; Chris Wilson; Christine Boyd; Christine Bronder;
The decision of the military regime to go ahead with the trial of Hariman Siregar, the first of the January 1974 tapols to come for trial , rather than hold these
In this study, we evaluated the performance of fi ve indices in predicting liver fi brosis grade, and we found that with the increasing hepatic fi brosis severity, as estimated by
Variance Estimation in Spatial Regression Using a Nonparametric Semivariogram Based on
As a continuation to the process started by medium dyadics satisfying linear and quadratic algebraic equations, the class of bi- quadratic (BQ) media is defined by requiring that
In summary, a three-fold increment in the prevalence of obesity and a two-fold increment in the prevalence of overweight were documented between 1994 and 2008
International Journal of Scientific Research in Computer Science, Engineering and Information Technology CSEIT1833608 | Received 01 April 2018 | Accepted 10 April 2018 | March April 2018