Early Blood Profiles of Virus Infection in a Monkey Model for Lassa Fever
Full text
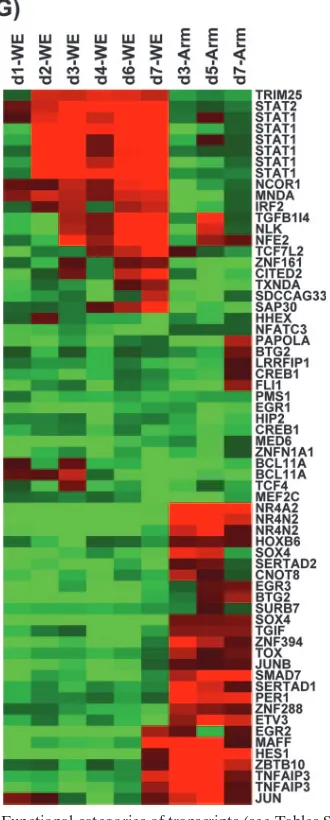
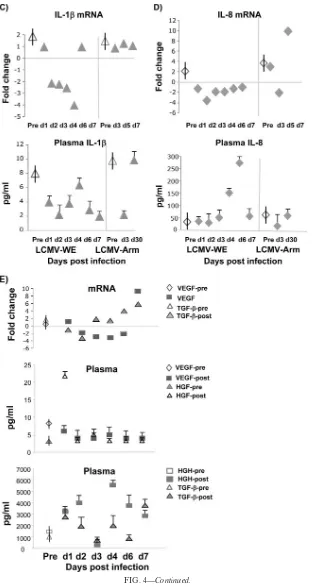
Figure




Related documents
Eighty-six percent of PGY2 residents reported being taught to discuss autopsy with the families of their pa- tients, and they came the closest to endorsing the state- ment, “I
Polar columns such as the Viridis UPC 2™ BEH column combined with a mobile-phase gradient of carbon dioxide and methanol provided the best separation of compounds in the mixture
Over 4000 British adults completed the Hogan Development Survey (HDS) (Hogan & Hogan, 1997) which measures eleven potential derailment behaviours (“dark side” traits) based
If a financial company being liquidated under OLA were a SIPC member, OLA seems to envision that some portion of its business would be liquidated according to SIPA under the
Non-orthogonal multiple access (NOMA) and device-to- device (D2D) communications have been recognized as promising techniques for the fifth generation (5G) networks due
For better communication wideband beamforming preferred over narrowband [8] by varying number of filer and its value adaptive antenna array used for different type
In particular, a given Near Neighbor query q with keyword set Wq, the query algorithm of I-index first by merging generates the set Pq of all points that have all the keywords of
The cloud storage is managed by the cloud service provider who provides storage service and the third party auditor (TPA), who has expertise and capabilities