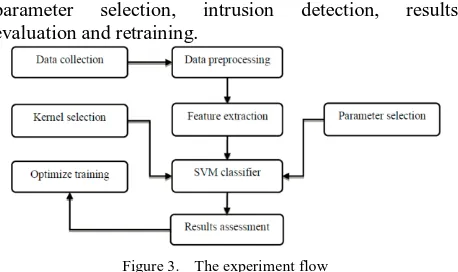
Efficient intrusion detection scheme based on SVM
Full text
Figure
Related documents
Because traditionally marketing is seen as a specialist function, we think that people that do marketing are trained as marketers so we don’t have to enable them?.
Layered Peer-to-Peer Mobile Service Broker Abstracting all the MSBs from the converged network architecture of MWS in Figure 1, we can get a layered P2P overlay network,
Instead of such a time-consuming nonlin- ear fit, which is not feasible for operational analysis of longer time series, the spectral effects of an ISRF change can also be accounted
As soon as possible contact WARSAW Approach after take-off on frequency published in ATIS if not otherwise specified by Tower.. Initial turns require bank angle
Le roulage sur les brins d’arrêt est déconseillé aux avions légers et aux avions ayant des petites roues ou une faible garde au sol.. Les distances déclarées ne prennent pas
When placed in water, cpnA ⴚ cells formed unusually large contractile vacuoles, indicating a defect in contractile vacuole function, while endocytosis and phagocytosis rates for
Silvio Luigi Feliciani.. THE BACHELOR DEGREEE PROGRAM IN THE MUSIC THERAPY COURSE OF THE CONSERVATOIRE OF MUSIC IN
Results: Having accounted for effects such as tree size and stand density, we found that: (I) tree species richness increased stand productivity in both countries while the effect