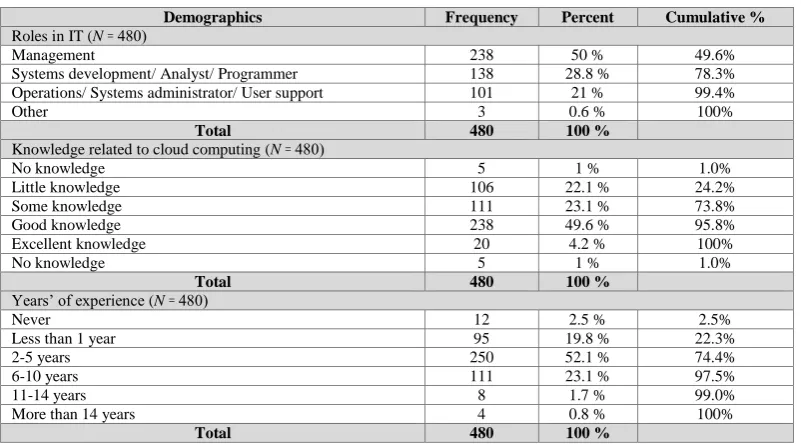
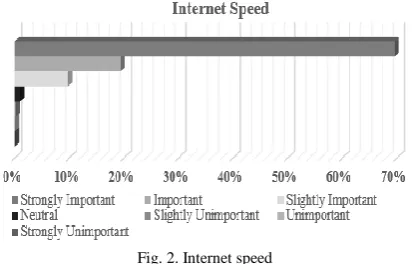
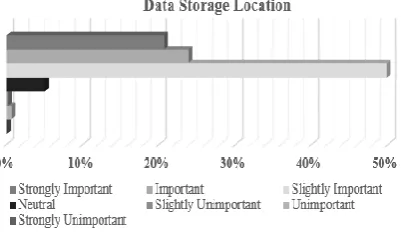
Factors to be considered in Cloud computing adoption
Full text
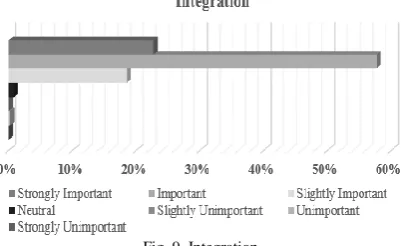
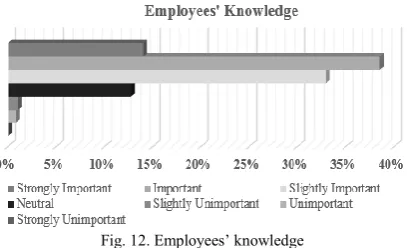
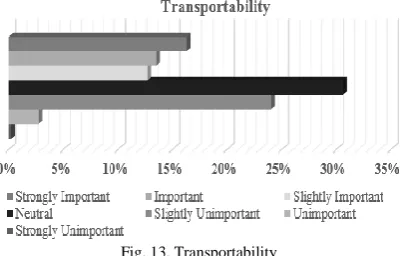
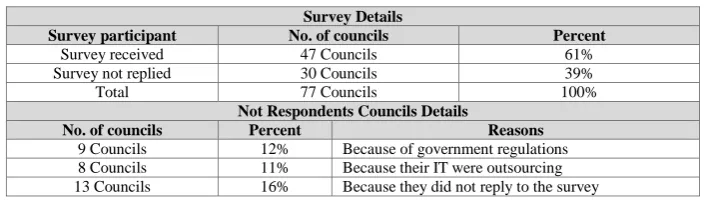
Figure
Related documents
1~ In contrast, it is reported that in mate- rials with irregular fiber distribution a bridging between the crack surfaces occurs: the crack propagation is interrupted by
TYPES Plain Chromic Braided Monofilament Braided Monofilament Braided Monofilament Monofilament Braided Monofilament Mulifilament Monofilament Braided Braided Monofilament
In this section, the dynamics and the cost functional of the original control problem are discretised in time and segment space. More precisely, we define a sequence of approx-
Drag the HTML object to your page in 90 Second Website Builder and double click it.. Enter a suitable
In this section, we present the classification derived in [ 89 , 90 , 91 ] for all topologically distinct gapped edges an abelian topological state can support when placed next to
Figure 5 illustrates the effect that ordering can have on the co- herence of the working set during an actual radiosity computation involving almost 2,000 clusters. Four permutations
By comparing the destination sequence number contained in RREP packets when a source node received multiple RREP, it judges the greatest one as the most recent
Long-term (9 yr) P leaching to the water table (3 m below the soil surface) at the field site was simulated with both one-dimensional (1D) and 2D models using the calibrated