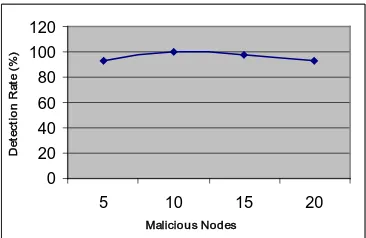
Protection of an intrusion detection engine with watermarking in ad hoc networks
Full text
Figure

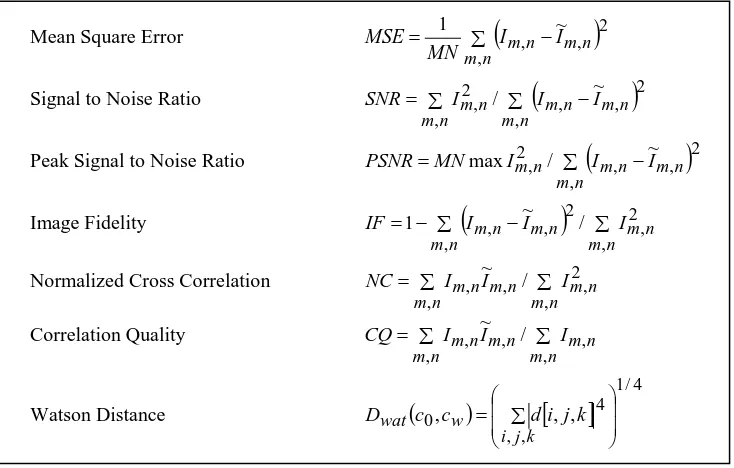


Related documents
Learning, knowledge and authority on site: a case study of safety practice.. John Rooke &
Table 3 shows that the specific gravity in day one to day seven, ranged between 1.45 to 1.43 in representative formula of Cefixime trihydrate, and 1.4 to 1.39 in marketed
We explore the relationship between ethnomethodology (EM), ethnography and the needs of managers and designers in industry, considering both ethnomethodological and industrial
Basalis epithelial cell proliferation in the wound area provides new cells in epithelial cell layer on top of granulated tissue.. Epithelial cells in this layer
The νCN vibrational band is not changed for all studied complexes, where the cyanide group is not involved in coordination, so coordination occurred through the carboxylic
Low toxicity, low cost, and biocompatibility makes them excellent candidates for in vivo bio-imaging, gene/drug delivery and cancer detection. This QD have too promised
A detailed analysis of Nurr1 expression in early and late embryonic stages of Uncx4.1 − / − embryos revealed that the loss of Nurr1 is consistent during midbrain dopaminergic
Successful toric intraocular lens implantation in a patient with induced cataract and astigmatism after posterior chamber toric phakic intraocular lens implantation: a case