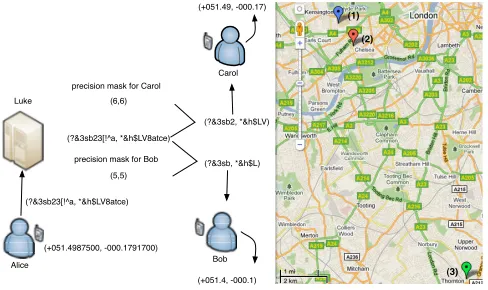
Longitude : a privacy-preserving location sharing protocol for mobile applications
Full text
Figure



Related documents
(B) The average neutron multiplicity per fission as a function of the heavy fragment mass from this study compared to data from Refs.. The dashed red line indicates the
Genome-wide association analysis of chronic lymphocytic leukaemia, Hodgkin lymphoma and multiple myeloma identifies pleiotropic risk loci..
Methods: We collected data from 1400 patients (1042 patients with confirmed unrelated Duchenne muscular dystrophy [DMD] or Becker muscular dystrophy [BMD]) registered in the
R90T was then compared against the WT-H7 using the hTLR5 clone in HEK293 cells and analysis demonstrated signifi- cantly reduced NF-kB dependent SEAP production over a range
In conclusion, while the analysis in this article cannot fully articulate the underlying drivers behind societal changes such as decline in marriage or lower total fertility, it
The existence of a correlation, rPp, between mated individuals, based on their somatic resemblance, means not only that there is a tendency to mate individuals of
Replacement of Cement by Various Percentage of Phosphogypsum And Flyash In Cement Concrete“, International Journal of Engineering Research and Applications Vol. Sudarsana Rao, H ,
The phenotype of this patient shows great similarity with the previously reported patients who have either a duplication or a deletion in this region, in- cluding a long face,
