Adaptive authentication and key agreement mechanism for future cellular systems
Full text
Figure

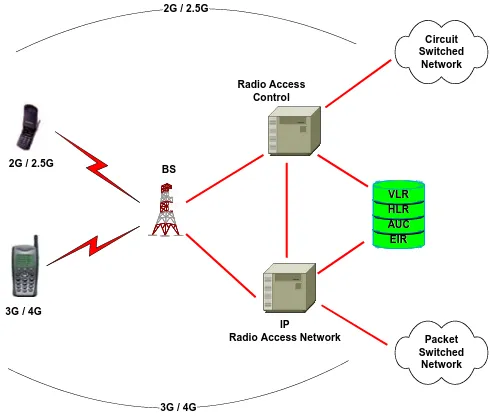


Related documents
This document is intended merely as a summary of the Platinum Plus health care plan offered by the Southern California Drug Benefit Fund.. For exclusions and restrictions, you
A.S., Southern University at Shreveport B.S., Northeast Louisiana University American Medical Technologist (AMT) Clinical Lab Scientist – Generalist, State License
Providing consultative and training services to school personnel and caregivers of children with Autism Spectrum Disorders.. Center for Autism and Related Disabilies, University
Considering the complete panel, the stained-glass win- dow in the Dining room showed a similar surface tem- perature during the night, independently of the glass color (Fig. 4 a,
Specifically, we consider optimal choice of the tightness, of the lag length and of both; compare alternative approaches to h -step ahead forecasting (direct, iterated
Investment in Companies active in Big Data management and Cloud Computing. Lerner, Christensen et al., 2012, The Impact of P olicy Changes on Investment in Cloud Computing
Social applications, collaborative applications, social search, threshold algorithms, context-aware search, query processing, cached results, views, signed networks, Wiki- pedia,
An analysis of the economic contribution of the software industry examined the effect of software activity on the Lebanese economy by measuring it in terms of output and value