Exploration of GPU Cache Architectures Targeting Machine Learning Applications
Full text
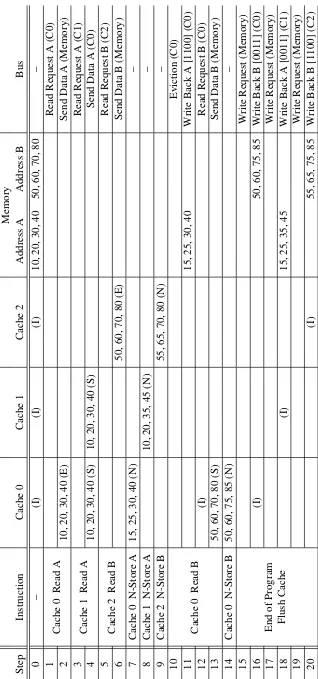
Figure


![Table 2.5: State Transitions for NMOESI Protocol [2]](https://thumb-us.123doks.com/thumbv2/123dok_us/62679.5874/29.612.118.536.92.306/table-state-transitions-for-nmoesi-protocol.webp)

Related documents
Processor Main Features Intel Extended Memory 64 Technology, Intel Execute Disable Bit Cache Memory 1 MB L2 Cache. Cache Per Processor
Performance was a major concern with the initial iteration of the scanner tool. All libraries used by the monitored program must be input into the tool. At the very least this
To master these moments, use the IDEA cycle: identify the mobile moments and context; design the mobile interaction; engineer your platforms, processes, and people for
In the Channel-SLAM algorithm [7], [8] summarized in Section II, every signal component, or propagation path, corresponds to one transmitter. However, the KEST algorithm may lose
Market Infrastructure: Clearing & Initial Margin CC P2 C Options Clearing Corp (OCC) CP1 CP2 CP3 CP4 Firm Firm Firm Firm Firm Firm Firm Firm Firm Firm.. CP Risk Management :
Read from main memory by processor 0 of the blue line: line is dirty (contained in P2’s cache). Request: read
South Asian Clinical Toxicology Research Collaboration, Faculty of Medicine, University of Peradeniya, Peradeniya, Sri Lanka.. Department of Medicine, Faculty of
surplus is given in equation (9). This completes the proof. Note that at this optimum tariff on low quality imports, profit of the domestic output firm falls to zero. This