An Options Approach to Cybersecurity Investment
Full text
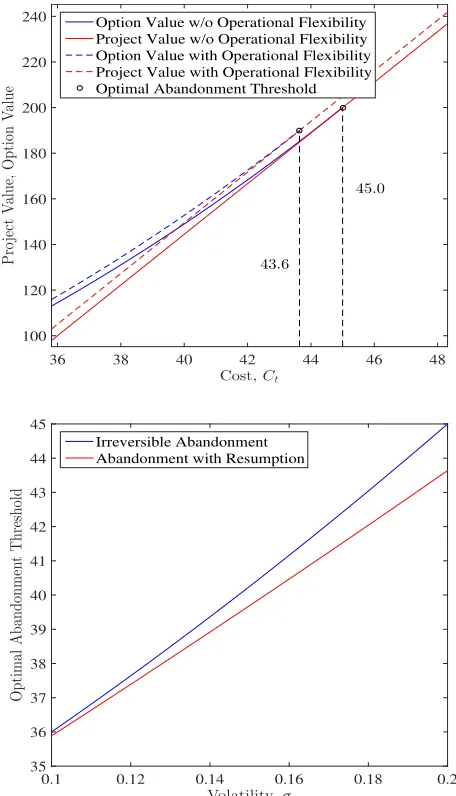
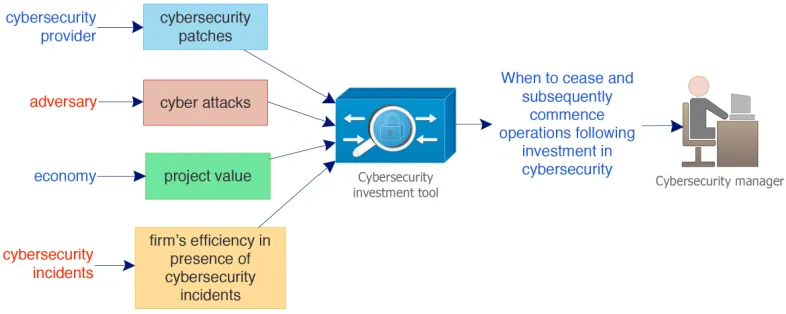
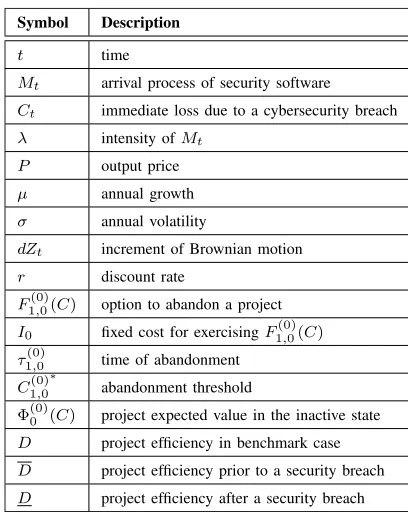
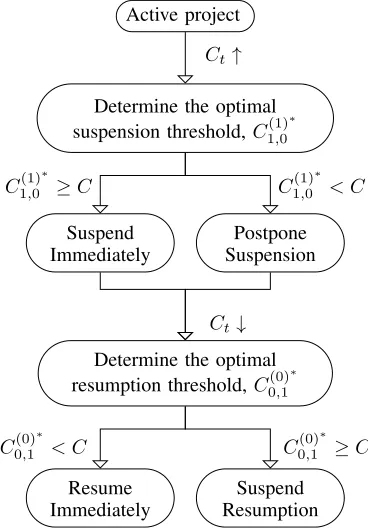
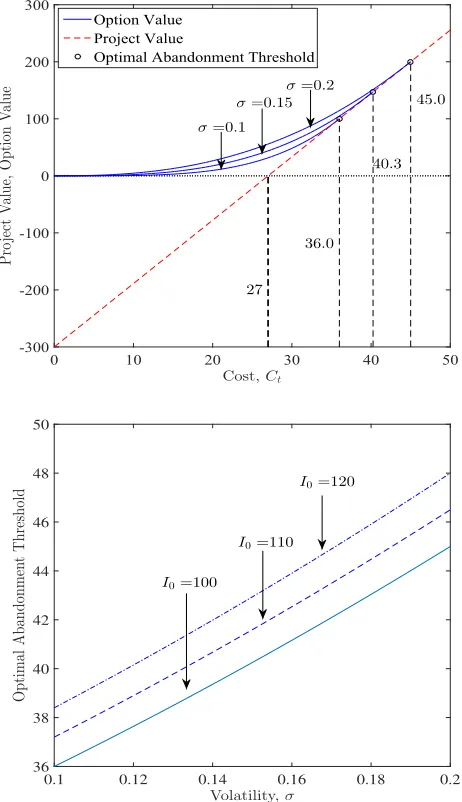
Figure
Related documents
The election of Joko Widodo in 2014 presidential elections is a strong testament to Indonesia's democratic values as it marked the first time when a twice-elected president handed
His research interests are mainly in Metaphysics, Philosophical Logic and the Philosophy of Language; but he is also interested in topics in the Philosophy of Mind, the Philosophy
on contemporary professional staff in higher education in the UK, the USA and Australia and identifies categories of professionals she describes as bounded, cross bounded
2 Write chemical formulas for water, carbon dioxide and hydrochloric acid.. 3 What is
Although many healthcare institutions have adopted electronic medical record (EMR) systems, the goals of comprehensive, continuous and patient-centered care have
Fruit parameters like fruit length, fruit breadth, fresh fruit weight, juice weight, peel and seed weight recorded significant variation with varying training systems (Table
(6) Best practice: (a) signature of the legal representative + common seal/contract seal; or (b) signature of an authorized person + common seal/contract seal + authorization
For both cases, Telair leveraged SIPSTACK’s ability to seamlessly integrate with third-party applications to provide each customer with the exact customizations they needed.