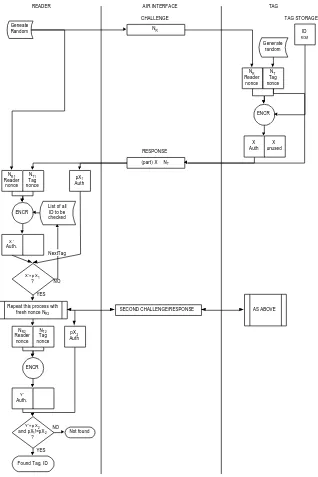
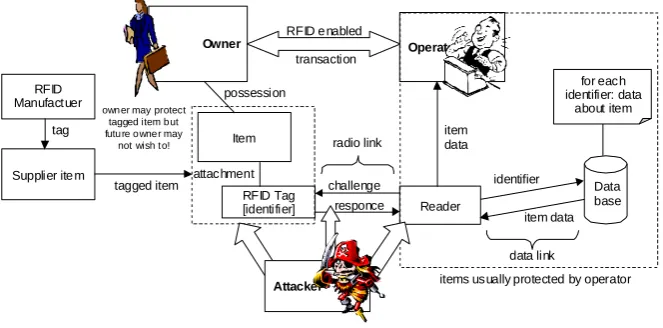
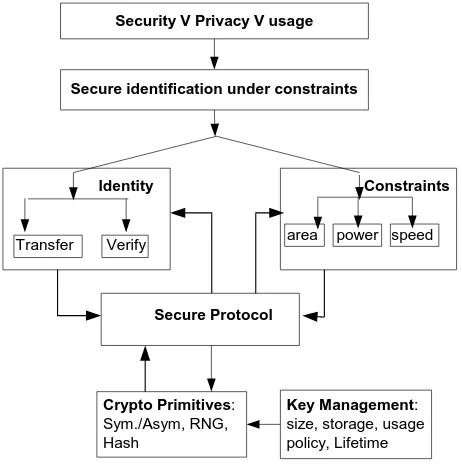
A holistic approach examining RFID design for security and privacy
Full text
Figure


Related documents
When selecting new primary care physicians, half of all consumers relied on word-of-mouth recommen- dations from friends and relatives, but many also used doctor recom-
be a powerful driver of quality improve- ment, but that providers seeking to improve quality need access to more granular data than the information publicly reported on
In particular we show that (1) manual counts of wildlife in satellite imagery can vary significantly between observers, and importantly observer confidence may differ between
Location: Sevilla, Spain More information: http://recruitment.jrc.ec.europa.eu/?inst=3582&type=AX&category=FGIV Contract Staff (M/F) Financial assistant
field experiment was conducted to study the impact of various sources of organic manures viz., sole application of composted pressmud, vermicompost, sewage sludge and farmyard
In summary, re-thinking residential mobi- lity as a relational practice can enrich the life-course perspective by providing a richer conceptualization of how (not) moving is bound
Clear Pavement-Bridge Dissipating Cure @ White Pavement-Bridge Dissipating Cure @ Clear Pavement Cure (non-dissipating) @ White Pavement Cure (non-dissipating) @...
Leveear er langsgåande ryggar på sida av skredløpet, medan lobe er ei tungeliknande form på skredavsetninga lengst nede i skredløpet (Blikra & Nemec, 1998). Denne