Architecting the Cloud Design Decisions for Cloud Computing Service Models pdf
Full text
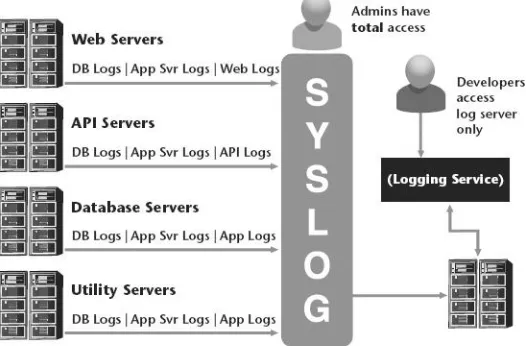
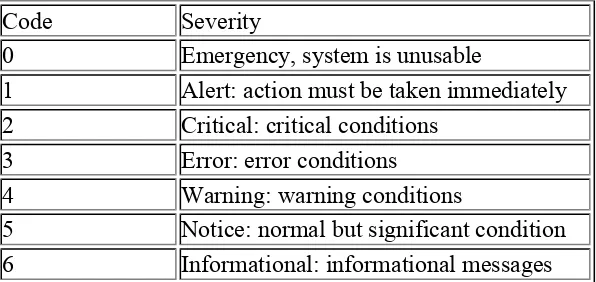
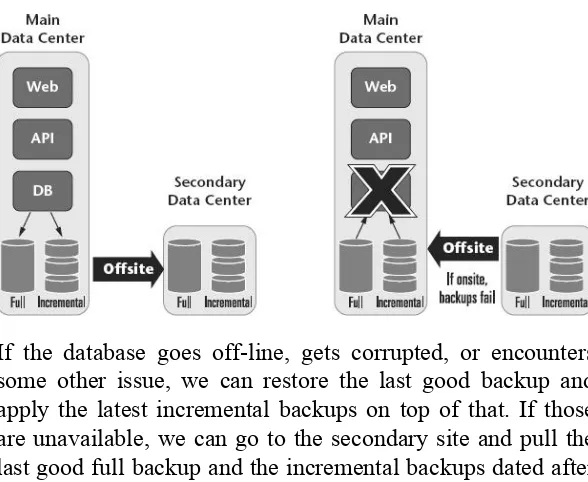
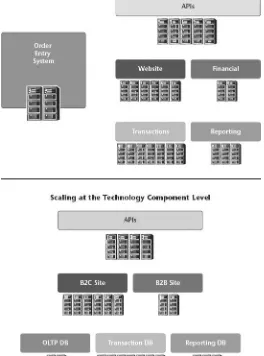
Figure
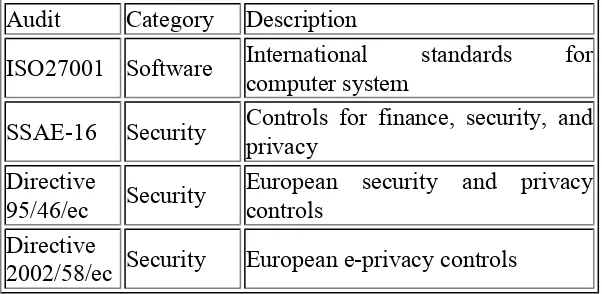
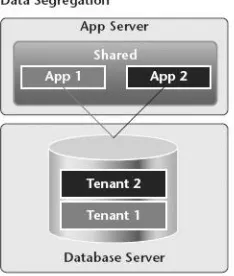
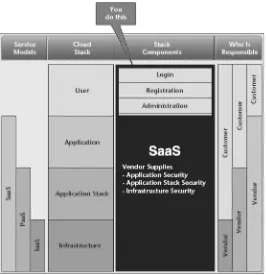
Related documents
However, the ability for unions to reduce injury rates does not appear to increase monotonically as they progress along a workplace instrumentality continuum from recognition alone to
Although there is very limited developmental evidence on this faculty, it should come as no surprise that anticipated regret, with its associated demands in thinking about
When analysing changes occurring in the milk yield and composition depending on successive lactation it was concluded that the highest amount of obtained milk, calculated FCM and
41 Buzzwords in eCommerce BIG DATA mCommerce personalization integrated marketing recommendation marketing automation. programmatic
Choral Director of Treble Ensemble, Chamber Singers, Male Choir, and Choral Accompanist, Downers Grove South High School.. Downers
The central finding of the paper is a general existence re- sult: there always exists a sequence of payoff-improving trades that leads to a stable vote allocation in finite time,
In models of money supply growth ∆m, output growth ∆y, inflation ∆p, fluctuations in an interest rate ∆r and a rate spread rr, however, we find only one case in which
As the evolution of these factors may influence the breast cancer burden, we examined both age at first menstruation and age at onset of regular cycling in a large sample of