SSH, The Secure Shell The Definitive Guide pdf
Full text
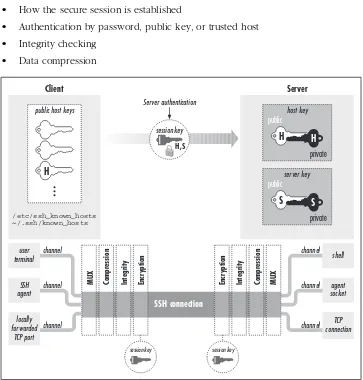
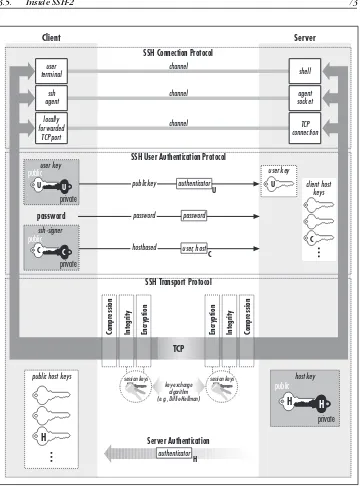
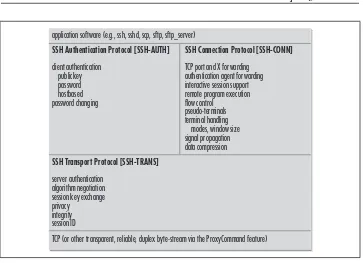
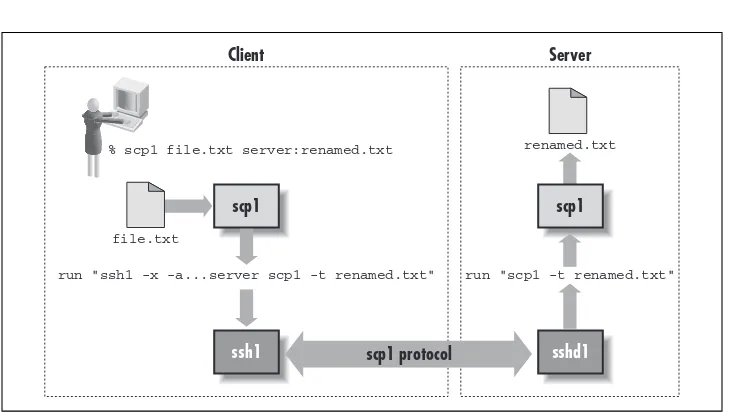
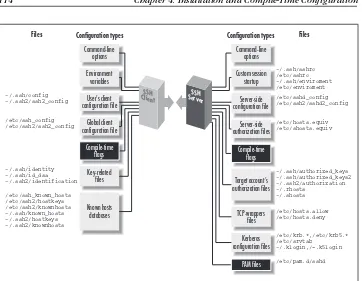
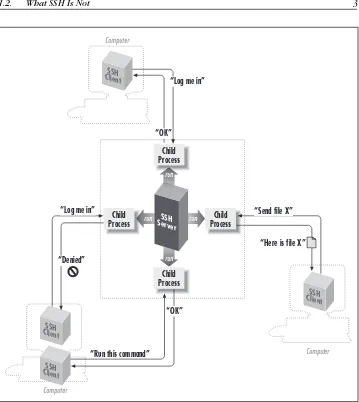
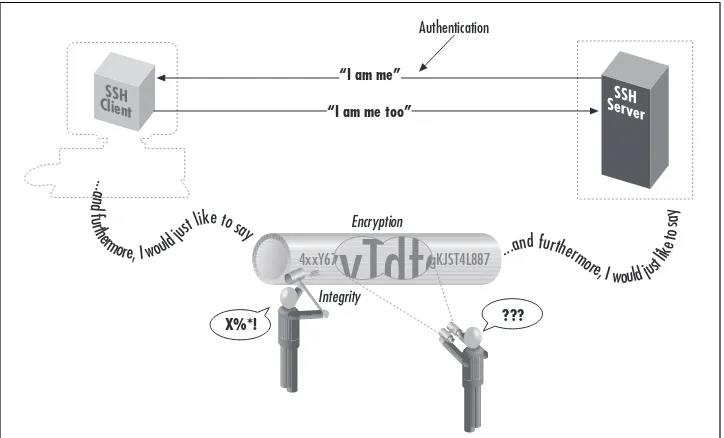
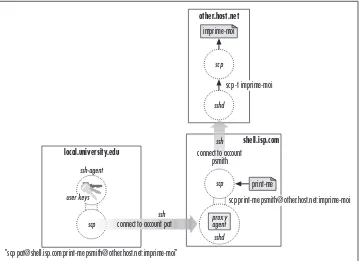
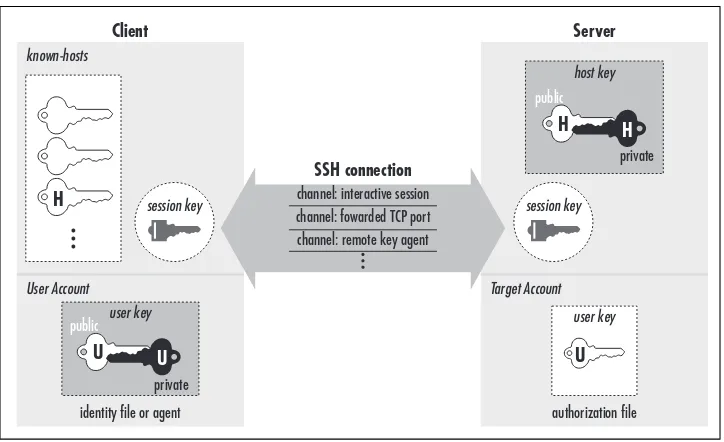
Figure
Related documents
person or persons shall execute the same as lessor, and the lease or contract executed by such person or persons shall take effect in all respects as if he or
Here, we carried out a high-density SNP-based case-control association study (N = 1262 [LOAD, 547; control, 715]) using 260 SNPs for an approximately 200 kb genomic region comprising
The goal is to make the best use of our facilities to support teaching and research, to provide the College with policies that allow optimal planning, and to inform the
We showed how habits and the consequent swings in risk appetite affect welfare and highlighted several ways in which movements in asset prices could be incorporated in monetary
Source: Joseph Pechman, Federal Tax Policy, Washington, DC: Brookings Institution, 1987. Does not include add-on minimum tax on preference items or alternative
This application note provides an overview of the Alcatel-Lucent Application-Assured Business VPN Services (AA-BVS) solution and the role that reporting and service
MOVE-SCP waits in the background for connections, will accept associations with Presentation Contexts for the SOP Class of the Study Root Query/Retrieve Information Model –
Laparoscopic Adjustable Gastric Banding patients will be frequently followed that includes clinic visits with the surgeon and Bariatric Program staff every 2 weeks for the first