Abstract : Federated cloud is the interconnection of transport on more administration furnishes with the assistance of representatives and agent administrators. Every supplier speaks with specific specialist, data with agents intermittently refresh with the dealer administrator vault. Administration gives are shortlisted by the agent chief client and ideal supplier is chosen. The client undertaking is doled out and the execution is assessed dependent on the administration estimation. List recommended by CCSMI. In this paper, the trust of the suppliers in federated cloud is estimated dependent on the estimation of trust, supplier is appointed for the client undertaking. The prerequisites to help united distributed computing situations are finding, positioning and choosing the suppliers and improves its execution. In this paper, fuzzy irregular hypothesis idea in the supplier and connected to register the most think the suppliers and chose ideal supplier. To lessen the plan multifaceted nature, layer engineering is proposed for federated cloud that comprises of use layer, administration deliberation layer, dealer layer and framework layer. Framework layer depicts the bolstered projects and assets in the suppliers. Representative layer clarify the league between the suppliers. Administration deliberation layer delineation the SLA the executives, adaptation to non-critical failure, chance administration and the idea of positioning the suppliers. Application layer bargains the upheld application in federated cloud. A hazard based access control system is proposed to deal with the entrance to assets by collecting the hazard measurements characterized in hazard arrangements made by the proprietor. Metaphysics is utilized for the proposed access control models to give adaptability and dynamism. Blame tolerant idea is recommended to oversee administration execution and administration infringement. Trust estimation of the suppliers are registered utilizing common propelled calculations, for example, Binary cuckoo hunt and Bee province streamlining, in view of estimation of must, suppliers are shortlisted, positioned and ideal supplier is to be chosen and productivity of the Proposed framework is demonstrated.
Key Terms: Federated Cloud, Trust Formulation and Computation, Service Level Assessment, Quality of Service.
I. INTRODUCTION
Cloud computing faces many challenges. These demanding situations encompass safety, privacy and consider. Among these, constructing agree with among individuals of the cloud might be a primary difficulty that hampers extensive use of cloud services. In general, patron
Revised Manuscript Received on April 07, 2019.
A. Mary Odilya Teena, Assistant Professor, Department of Computer Science, St. Joseph‘s College of Arts & Science (Autonomous), Cuddalore &
Ph.D. (Category-B), Research Scholar, Bharathiyar University,
Coimbatore..
Dr. M. Aaramuthan, Associate Professor & Head of the Department of
facts square degree keep in the Cloud Service Provider‗s (CSP) premises, wherever clients have little or no management over the technique their statistics is treated. Trust is extensively talking cited commonly computing literature; however, in the cloud computing putting it's nonetheless partner in nursing elevating subject matter [1]. This paper investigates however cloud customers necessities have an impact on their believe in a totally provider, and proposes taxonomy for comparing believe [2].
During this work, we will be inclined to suggest a framework and a mechanism that live the standard and range Cloud services. .Such a framework will build a big impact and might produce healthy competition among Cloud suppliers to meet their Service Level Agreement (SLA) and enhance their QoS [3]. The Ranking System computes the relative ranking values of assorted Cloud offerings supported the QoS desires of the customer and alternatives of the Cloud services [4]. Cloud based totally believe management models may be categorized onto four absolutely exceptional classes: i) coverage, ii) pointers, iii) name and iv) prediction based totally. In policy based totally consider control fashions, there is a collection of policies assumes a collection of authorization tiers with minimal trust thresholds. The thresholds might be decided mistreatment,
a) Observance and auditing approach (E.g. Provider stage settlement violations),
b) Entity believability technique (E.g. C program language period, availability) or
c) Comments believability (e.g. Trustiness, understanding) strategies.
Advancement of distributed computing are normally inferred back to sixties of residual century, anyway till the twenty first century, distributed computing is broad respected basic, and a little bit at a time come to be the possibility of the long haul improvement course. Individual distributed computing is AN augmentation of distributed computing inside the non-open area, in light of Internet-driven overseeing of non-open records. In other words, non-open distributed computing sorts out, shops, disseminates and reprocesses a number non-open data through the Internet [5]. The improvement of agree with, its importance and function has been acknowledged, checked out, and stated in numerous courses for the reason that floor-breaking paintings by way of Barber. Trust has been investigated in several contexts, collectively with
virtual organizations and international environments
Federated Cloud Selection, Formulation And
Computation Using Service Level Agreements
And Rank Based Selections On Fuzzy Sets
Based Selections On Fuzzy Sets
here is on cloud computing, and that we explore the cloud-precise elements. A popular and complete discussion of believe is at the some distance side the scope of this paper. Trust is Associate in nursing essential detail of human relationships, and it's wished for accomplishing human interactions. Likewise, inside the subject of era, accept as true with is essential for gambling virtual interactions as an example, even as no longer trusting a web banking provider; the bank‗s customers may not make use of the provider [8]. As a final product of the Brobdingnagian assorted variety inside the gave Cloud administrations, from the customer's motivation of inspect, it's come to be hard to make your psyche up whose administrations they should utilize and what is the reason for their decision. As of now, there might be no system that may allow customers to assess Cloud contributions and rank them bolstered their ability to meet the client's Quality of Service (QoS) wants.
II. PROBLEM STATEMENT
A Cloud enterprise can be characterized as extraordinary server farms having a location with numerous CSPs associated out and sharing their belongings to convey powerful administration execution. In a federated Cloud, property are generally dispersed and overseen among CSPs concerning unique factors, for instance, asset usage, neighborhood workloads, and lawful issues. In this unique condition, relegating the Cloud blessings which might be required to convey an utility to various frameworks inside the alliance in mild in their safety prerequisites may want to accomplish the perfect security degree this is required for the utility in order to paintings accurately. Improving the safety of an utility is chiefly in mild of three viewpoints:
i. Limiting the safety cost due to security overhead what's greater, misfortune coming about due to security disappointments,
ii. Giving the application with an appropriate level of protection execution, for the reason that giving decrease or large amounts can set off specialized or on the other hand money associated misfortunes,
[image:2.595.323.529.60.235.2]iii. Sending the utility with negligible risk chance. For example, disappointments in statistics insurance or then again accessibility due to decrease than required protection levels can hurt the software's dependability and purpose a drop in the quantity of customers; the software might also likewise revel in the ill consequences of Quality of Service (QoS) corruption due to over-security that may be on occasion superfluous, which can motive Service Level Agreement (SLA) infringement.
Fig 1.1 Federated Cloud Model
The value is assessing the trade off to contemplate between the safety elements amid advantage mission, and run an association of reenactments to assess the execution of our model. In this segment, we advocate the enhancement show. To chose to make use of Multi-Objective improvement due to the fact the problem consists of enhancing one of a kind factors (in a few instances clashing) amid the project technique. The contribution to the enhancement show comprises of: 1) the security highlights and parameters given by way of the league server farms (records identified with protection measurements), 2) the safety conditions of the purchaser, moreover, three) the security and execution obstacles inferred from the SLA and Security-SLA. The yield is an arrangement of plausible perfect Cloud benefit to-server assignments that are in reality meditated via the provisioning of VMs.
Fig 1.2 Cloud Content Delivery Network Services
Even though respectable quantity of analysis has been conducted in fuzzy based totally cloud computing with the aid of addressing the significance of fuzzy and suggesting new solution to the matter in cloud computing, we generally tend to nevertheless have a few troubles that require being address in greater studies. Virtualization is to reinforce the employment of assets and minimize the operation charge in DCs of clouds. Completely distinctive form of enter parameters vicinity unit taken to comprehend the above mention objective, however we want to consider the complete software running on the top layer of VM for choosing the suited bodily system for hosting the ones VM. It allows the threat to consider the communication reliance among VM in a couple of degree corporation utilization and additionally the simple DC network topology and maximum limits of bodily system within the DC.
i. Varied fuzzy VM migration techniques exist for migrating VM to minimize the energy consumption. Currently, cloud Sim is employed as popular framework to show the pleasant of models. We need to judge those models with other form of utility retaining unsure employment surroundings. Intensive evaluation is performed to digital system migration anywhere the entire fashions place unit carried out in single cloud. That is, migrating the of VM takes place the various DCs of a specific cloud, we need to redesign the algorithmic rule which could applied in inter- cloud to get to the bottom of the migration issues.
ii. Completely extraordinary models place unit developed to overcome the uncertainty and first-rate between cloud provider provider and cloud carrier person relating to services great. Differing sorts of attributes location unit idea-approximately for diverse fashions. Extensive evaluation is wanted to conquer the dual problems so one can occur among cloud service supplier and user and knowledgeable approach vicinity unit had to gauge the entire great version. iii. Majority of analysis victimization mathematical common sense is carried out within the area of aid improvement, scheduling, and repair dependability in cloud computing, But, they need unheeded the vicinity of know-how garage and protection in cloud computing the usage of mathematical logic. Deep analysis is wanted to beat the problems in statistics garage and safety [16].
III. LITERATURE REVIEW
A variety of researches had been proposed by way of
analyzed and interpreted the scheduling framework and cloud brokering. Following are the literatures applied for assessment of the cloud computing. Based at the framework and cloud brokering, demanding situations and safety of cloud providers, complete literatures are analyzed.
C. Esposito, et al. [8], inform that, this paper offers a consider management version supported multi-agent and agree with analysis. It adopts the centralized distribution control mode and sets up multiple 1/3-celebration marketers within the cloud; what's greater, it's going to manipulate the customers and cloud services through the collaboration of the sellers correctly. By victimization multiple 0.33-celebration agents, it's going to reduce back the single-agent‗s strain of computation, garage and also the user‘s waiting time. The test indicates that the believe management model is effective. M. J. Good and L. Le et al. [36], recommended as another processing mode, distributed computing will offer clients with virtualized and ascendible web contributions, that treat went up against with extreme security requesting circumstances, however. Access control is one a portion of the critical measures to check the security of distributed computing. Anyway applying memorable gain admission to power show into the Cloud straightforwardly couldn't clear up the vulnerability and powerlessness on account of the open states of distributed computing. In distributed computing environment, best the insurance and duty of every interchange occasions are guaranteed, insights wellbeing are regularly proficiently justified amid communications among clients and subsequently the Cloud. In this manner, assembling a shared consider seeking among clients and cloud stage is that the way to put in power new assortments of gain passage to power technique in distributed computing environment. Consolidating with Trust Management(TM) [13], a shared consider principally based gain passage to power (MTBAC) display is arranged all through this paper. MTBAC show take every buyer's conduct acknowledge as valid with and cloud contributions hub's high caliber into thought. Trust connections among clients and cloud bearer hubs are mounted through shared trust instrument. Security issues of gain admission to power ar fathomed by methods for forcing
MTBAC demonstrate into distributed computing
environment. Reenactment tests show that MTBAC rendition will guarantee the association among clients and cloud transporter hubs.
F. Tasi and Kuntai et al., Du tells that, In distributed computing, acknowledge as valid with control is loads of important than any time in recent memory sooner than in the utilization of data and discussion advancements. Inferable from the dynamic idea of the cloud, nonstop recognition on consider credits is basic to actualize supplier level assentions. Ivey et al. , suggested that, this paper tends to the matter of determinant quality of Cloud Service Providers (CSPs) in an exceedingly cloud setting. For the present work, quality is illustrated on the grounds that the certificate of consistence of a CSP to the comfortable quantitative QoS parameters as plot inside the Service Level Agreement (SLA). As a result of incredible amount of CSPs
Based Selections On Fuzzy Sets
the cloud setting, it is turned into an intense mission for Cloud buyers (CCs) to spot and separate between the honest and untrustworthy CSPs. At blessing, there's no consider investigation gadget that enables CCs to choose the attribute of CSPs on the reason in their adherence to the SLA i.E. The consistence outfitted by method for the CSPs to CCs as reliable with the SLAs.
Wang, Raverm, and R. Ranjan et al this paper proposes a Compliance-based absolutely Multi-dimensional Trust assessment System (CMTES) that enables CCs to see the attribute of a CSP from absolutely extraordinary points of view, as consider can be an abstract hypothesis. Such a framework is of wonderful encouraging to CCs UN office want to settle on a CSP from a pool of CSPs, satisfying their favored QoS necessities. The structure licenses U.S. To pick the attribute of a CSP from the CC's point of view, Cloud Auditor's frame of mind, Cloud Broker's edge and Peers' viewpoint. Test outcomes demonstrate that the CMTES is successful and strong in separating genuine and temperamental CSPs. The approval of the CMTES has been done the assistance of engineered data because of absence of institutionalized dataset and its relevance has been incontestable with the assistance of a case investigate concerning the utilization of real cloud measurements.
IV. CLOUD TRUST FORMULATION
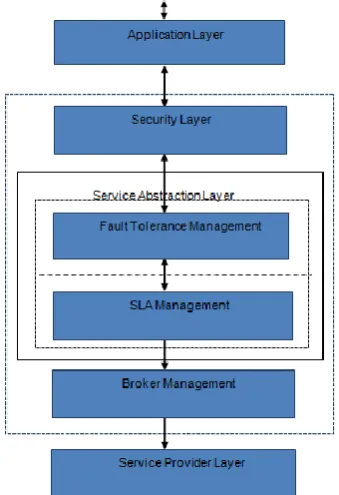
[image:4.595.348.518.66.314.2]Federated Cloud Architecture (FCA) is described as the interconnection of two or greater Cloud Service Providers (CSP) that is accessed by means of specific agents and all agents statistics are collected and up to date periodically within the registry broking manager. Initially, carriers are observed for the provider the use of dealer learning algorithm, rating all of the observed vendors, and selects and assigns the most effective company for the provider. Now a day, single company might not be sufficient to satisfy the requirement of the user and alertness. In this example, FCA is the best opportunity to encounter the desires of the customers. As of late, more prominent analysts appearing on this spot and supporter part of successful responses to perform Quality of Service (QoS) based supplier choice from the pool of CSPs. Cloud Service Measurement Index Consortium (CSMIC) [7] analyzed Service Measurement Index (SMI) measurements that encourages to assess and assess the administrations of various CSPs. Compelling decision designs offer perfect cloud administration to clients are high require the developing assortment of cloud benefits on the cloud stage. In this chapter 11, Trust essentially based cloud decision rendition is proposed to find the suppliers for the bearer and assess the administration the utilization of the idea of Fuzzy Random Theory. The present strategies depend on the QoS ranking to select the CSP and forget about the accept as true with relationships amongst customers, agents and CSP. The proposed cloud issuer provider selection version integrates the QoS and accept as true with courting of CSPs and customers.
Fig 1.3 Cloud Trust Formulation and Service Levels The phases inside the existence cycle of SLA control are layout and development, provider imparting, carrier negotiation, provider provisioning, service operations and carrier decommissioning. The existence cycle of SLA brings carrier expectancies, drive engineering selections at design level and operational choices at the extent of utilization and shipping. Users set up the agreements with one or extra vendors based totally at the requirement and importance of the service thru the method of SLA negotiation. If there is any violations in the SLA life cycle, with the aid of considering the importance of SLA, fault tolerance enabled SLA service is usually recommended inside the proposed architecture.
Coordinating Provider Values = QoS, C, CFP and Inputs MP means the Matching supplier for the supplier. QI is the posting of Quality Indicator recognized by method for the SMI. FA talk the useful necessities.RCP alludes the guide request by methods for the transporter and propelled with the guide of the organization.
Fig 1.4 Cloud Formulation Each Levels of Services with Data set as input
1. First, every supplier is practically grouped dependent on the build up assentions in SLA.
2. Second, the comparability of the supplier is registered dependent on the SMI characteristics, for example, reaction time, interoperability, confirmation, security and protection and ease of use.
3. Service assignment is ordered as least required, greatest required
4. Initialize bumble bee parameters are mapped with combined cloud n= number of utilized honey bees as suppliers
5. Construct beginning supplier for introductory arrangement All assignments find reasonable supplier for its execution
m = Number of passerby honey bees (m>n) as assignments
s= number of scout honey bees as limit of assets.
Emphasis: Maximum cycle number
α : beginning estimation of punishment parameter
Algorithm for computation and evaluation
Register the comparability ojf the suppliers by finding the wellness capacity of the supplier Set of errands T = {T, T, T}.
1 2 n 2 n
Due date of undertakings D = {D1,D2,… Dn } Let SP = {p ,p , . . . p }
1 2 m
All out assignment culmination - TCT. Finishing time of
TCT= max {CT ij|i ∈ T, i = 1, 2 . . . n and j ∈ VM, j = , 2, . . .
m} Min j= 1….m Capacity of provider‗s pj
pj = PEnumj × PEmipsj + VMbwj
PEnumj is the number processor in providerj
PEmipsj is million directions executed every second in providerj Ubwj is the ease of use of the supplier
Total length of tasks that are assigned
All out length of undertakings that are doled out to a supplier is called ease of use of the supplier. Ease of use of the supplier can be determined as the quantity of undertakings at time t on the supplier
U =Processing time of a provider
Fitness function = +
Appoint assignments to supplier as indicated by probabilities. For all errands ,Construct arrangement utilizing undertakings All undertakings find appropriate supplier for each errand. In the event that fit(task)>fit(provider)
Discover best supplier, supplant with separate undertaking. Whenever fit (task)<fit(provider) Find best practical undertaking, supplant with Best arrangement,
End For
Instate scout honey bees Construct arrangement utilizing assignments
Whenever fit (resources)> fit (supplier) The asset supplant supplier n=n+1
Until (n=provider)
This proposed works of art presents asset proprietors and Federated Service Provider (FSP) additional oversee over the adaptability of approval. This system incorporates Risk Engine, Risk wellbeing Functions, Risk Policies, and Risk assessment unit. Hazard Engine is in charge of breaking down and preparing the danger strategies related to a valuable asset and for conjuring wellness capacities delineates in every strategy. In present work, Risk Engine is outstanding for each FSP on the grounds that it actualizes the wellbeing trademark in that guarantor. In the proposed artworks, Risk Access Control Mechanism is to be had inside the middleware layer; go about as a different part and tantamount for all SP in combined structure. Hazard inclusion is a XML record clarifies how chance based absolutely inspire section to control is appointed for each guide. Hazard wellbeing highlight is the registered capacity that actualizes the hazard measurements which can be accessible to be utilized in the peril approaches. The hazard
Based Selections On Fuzzy Sets
asset doled out for the individual and takes decision including permit, deny, presently not appropriate and middle.
VI. COMPUTATION AND EVALUATION The standard of fluffy sets and fluffy capacities found valuable in applications, for example, design acknowledgment, bunching, data recovery, and frameworks investigation. The thought of fluffy irregular factors was presented as a characteristic speculation of arbitrary set so as to speak to relationship between the results of irregular analysis and non-measurable in careful information. Fluffy Set present the idea of a fluffy arbitrary variable as a capacity F: Ω→F(S) where (Ω, A, P) is a likelihood space and F(S) signifies all piecewise nonstop capacities U:S→[0, 1]. A thought of a fluffy arbitrary variable [14] marginally not quite the same as that of Fuzzy Values that it as a quantifiable fluffy set esteemed capacity x:Ω→F0(S), where R is the genuine line, (Ω, A, P) is a likelihood space, 0(S) = {A:S→[0, 1]} and {xϵS; A(x) ≥ X} is a limited shut interim for every X ϵ (0, 1). Give U a chance to be a nonempty regular set, P(U) signify the arrangement of all subsets in U and F(U) mean the arrangement of every single fluffy subset in U. For AϵF(U) we characterize two subsets of U as pursues:
Ai,j = {xϵU; A(x)≥ X} for any ϵ [0, 1], Ac = {xϵU; A(x)>S} for any ϵ [0, 1],
Where A(x) is the membership functions of A. These are known as S cuts of the fuzzy set A. Without loss of generality in the sequal Xi, Fi, Gi, Fi, Gi, denote the respective cut functions.
Ai,j = [A- , A+ ]
Where A, = inf Aj, A+,j = sup Aj
The suggested ranking model consists of three phases namely (i) Discover service providers (ii) Rank the selected service provider (iii) Choosing the best service provider. This ranking model has been working on the concept of fuzzy random variable.
VII. DISCOVER SERVICE PROVIDERS Cloud Broker manager selects the service providers, based on the service requirements and current status of service providers. CBM use the concept of fuzzy random model process, to select the service provider. A fuzzy random process satisfying the fuzzy Markov property can make predictions of the future process based on the present conditions. Consider user requirement parameters like availability, security, cost etc as Y. Broker
Manager as X, service providers as F (f1, f2 ... pf) and selected service provider as SP, then the stochastic Markov property is defined as
M {F ≤ X (P) / SP(Y) = P(Y)}
Selected service providers based on Markov process, are entered in the form of matrix called compatibility decision matrix. Compatibility decision matrix consists of n rows and 3 columns. Each row in a matrix gives the current status and availability of service providers. Three columns in a decision matrix represent the name of a service provider, status of service provider (eligible, ineligible) and availability of service provider. Availability of service provider is obtained from cloud table in CPM.
Rank the selected service providers using Fuzzy sets CBM chooses the best specialist co-op among the quantity of accessible and qualified specialist organization in the similarity choice lattice utilizing Fuzzy set technique. Established set hypothesis necessitates that every component of a set included totally inside the set. Fluffy set hypothesis, a speculation of established set hypothesis, enables set components to have incomplete enrollment and in this way permits portrayal of loose and subjective data in an accurate way [11]. There are various strategies for building up the extent of participation between two abutting sets. The fitting technique is dictated by the setting of a specific application. Sigmoid formed participation work is utilized to rank the cloud suppliers dependent on the accompanying measurements, for example, administration reaction time, manageability, appropriateness, interoperability, accessibility, unwavering quality, steadiness and cost. Administration reaction time is figured by methods for how quick the administration/assets can be alloted for use. Participation work is mapped to an enrollment esteem somewhere in the range of 0 and 1. Supportability alludes the ecological effect of the cloud administration utilized. Reasonableness demonstrates the necessity of client met by the cloud supplier. Exactness means the administration functionalities measures to the client's real qualities when utilizing an administration contrasted with the normal qualities. Interoperability is characterized as the capacity of an administration to collaborate with different administrations offered either by a similar cloud supplier or different suppliers. Accessibility alludes the level of time a client can get to the administration. Unwavering quality means how an administration works without disappointment amid a given time and condition. Versatility implies the capacity of the specialist co-op to alter changes in administrations dependent on client demands. The fluffy irregular enrollment work gives the most extreme detachment between those serials amidst the positioning framework, while those serials at either outrageous are grouped together intently.
To propose positioning component dependent on Fuzzy irregular methodology having three general stages, for example, issue decay, judgment of needs and conglomeration of these needs.. The accompanying enrollment fluffy irregular capacity utilized is given as underneath
Ai = {xϵU; A(x)≥} for any ϵ [0, 1], Ac = {xϵU; A(x)>} for any ϵ [0, 1],
To rank the specialist organizations, the administration usefulness characteristics are arranged into three classifications, for example, class A, class B and class C. Class An alludes abnormal state properties, for example, responsibility, affirmation, security and protection. Class B alludes next dimension characteristics, for example, ease of use, unwavering quality and Interoperability. Class C indicates low dimension traits, for example, client intrigue, dependability, Cost, throughput and proficiency. Intermediary is in charge of
cooperation with clients and understanding their demand
framework considered two viewpoints, for example, (I) the administration quality positioning dependent on Fuzzy set and (b) the last positioning dependent on the expense and quality positioning. Every property are joined with weight works and turn out to be anything but difficult to guarantee the accomplishment of the best trade off arrangement dependent on the goal work.
Positioning of Cloud administrations is a standout amongst the most difficult undertakings in the structure of cloud. The Ranking System processes the relative positioning estimations of different Cloud administrations dependent on the QoS prerequisites of the client and highlights of the Cloud administrations. To compute the choice of positioning the specialist organization utilizing two unmistakable edge esteems, at that point recalculated utilizing a fluffy set enrollment capacity to dole out the participation esteems for every one of the individual cloud supplier positioning criteria and after that utilized fluffy piece principles to join these information. At long last, the general positioning of the cloud suppliers are thinking about by the Class C level properties.
[image:7.595.305.565.51.167.2]VIII. SIMULATION RESULTS AND DISCUSSIONS Reenactment tests had been actualized on the Cloud Sim and Amazon Red Shit. n a pc whose setup was an Intel Core i5-3337UCPU 1.Eighty GHz, four GB RAM, Windows 7 (64 bits) working device, Service Pack 1.Average reaction time and throughput changed into figured and the execution turned out to be likewise dissected. The parameters mulled over for the recreation are amount of clients, scope of cloud transporter suppliers, cut-off date of assignments and so forth. The execution time for each endeavor is relegated haphazardly among 2 ms to 5ms. Number of clients considered are 1000,3000,5000,10000 at once. Number of administration transporters accessible is fixed as a 100,200,300 and cut-off date for each demand is fixed as 2.5ms. Each cloud administration organization has 150 processing has and a period shared VM scheduler. Cloud specialist in the interest of client ask for include 500MB of memory, 1.5GB of carport, 1 CPU, and time-shared Cloudlet scheduler. The broking demands instantiation of 50 VMs. The exploratory outcomes demonstrate that the proposed positioning model performs better as far as normal reaction time contrasted with the without positioning model in the Federated engineering. Recreation results are appeared Table 1. Normal reaction time is characterized as the time between when client asked for an administration and really open.
[image:7.595.307.570.412.629.2]Table 1: Execution Time measurements
Fig 1.5: QoS Measurements using Amazon Red Shit input based on Number of requests
The outcome demonstrates that the relegated cloud supplier fulfills the necessities regarding trust, security and execution. The overhead of the positioning component relies upon its execution. The characteristics in levels are alloted with steady and the execution time for performing positioning system for 500 suppliers is 10ms.The SMI attributes are considered for the proposed work. The proposed characteristics are taken by the reference of Amazon web administrations input Framework. Also the SMI characteristics which are basic for Heath mind cloud advantage as taken with an assistance of social protection master's info. Furthermore the Health mind specialists offered contribution to weightage of each property.
Trust Security
Absolute =QoS+CFP+C+Providers if total>=4 and complete <=5
Trust_Security = 1 low else if (complete >= 6 and total<=7)
Trust_Security = 0
Else
Security=high
Fig 6: Trust Security calculation using Amazon Red Shit
XI. CONCLUSION
In this paper, we discussed the cloud organization decision issue in a space where the requirements of customers keep developing.
We proposed a structure that finds a case of changing UPs Number
of users
Execution Time with Ranking
Model (ms)
Execution Time without Ranking
Model (ms)
1000 0.28 1.25
2000 0.75 2.73
3000 1.85 3.21
5000 2.53 4.58
[image:7.595.48.291.633.755.2]Based Selections On Fuzzy Sets
the fundamental customer tendencies. We by then discussed well ordered guidelines to pick legitimate Cloud organizations subject to the valuable and non-helpful requirements conveyed by cushioned (i.e., questionable or free) learning given by customers. Against this issue, we proposed a novel cushioned customer arranged Cloud organization assurance structure. (1) a soft Cloud reasoning that supports the closeness calculation of Cloud organization thoughts and the capable inquiry of Cloud organizations or organization associations that by and large arrange customer requested limits; (2) a feathery AHP approach that figures the heaps of the non-functional properties (i.e., organization situating criteria) to the extent customer tendency; and (3) a fleecy TOPSIS approach that rates the contender Cloud organizations subject to the heaps and the execution of the non-handy properties. In order to deal with the issue that the dynamic changes of cloud expert association organization capacities, vindictive customers trust appraisal, the introduction of the buyer faithfulness, the spoil time, the trade whole, the discipline factor for the explicitly steadfastness dynamic updates. Finally, generation examinations to check the proposed exhibit cloud trust detailing, calculation and assessment dynamically heartly, it not only can acclimate to the dynamic changes in the earth, yet notwithstanding ensure that the veritable idea of organization, blackmail and harmful appraisal of pernicious substances have a particular ability to face. The dynamic cloud organization assurance is required further improvement, the gathering of cloud organization provider's advantages, upgrade the customer input framework parameters to improve the organization requestor organization decision precision. Cloud organization assurance of execution, faithful quality and distinctive perspectives can be asked about extra start to finish later on.
REFERENCES
1. W. Liu, Y. Dong, F. Chiclana, F. J. Cabrerizo, and E. Herrera-Viedma,
―Group decision-making based on heterogeneous preference relations with self-confidence,‖ Fuzzy Optim. Decis. Mak., vol. 16, no. 4, pp. 429–447, Dec. 2017.
2. M. J. Moral and L. Le, ―A Comparative Study on Consensus Measures
in Group Decision Making,‖ Int. J. Intell. Syst. Press. 2017., Press, no. 1, pp. 283–287, 2017.
3. M. R. Asadabadi, ―A Markovian-QFD approach in addressing the
changing priorities of the customer needs,‖ Int. J. Qual. Reliab. Manag., vol. 33, no. 8, pp. 1062–1075, 2016.
4. S. Deng, H. Wu, D. Hu, and J. Leon Zhao, ―Service Selection for
Composition with QoS Correlations,‖ IEEE Trans. Serv. Comput., vol.
9, no. 2, pp. 291–303, Apr. 2016.
5. W.-C. Lin, S.-W. Ke, and C.-F. Tsai, ―CANN: An intrusion detection
system based on combining cluster centers and nearest neighbors,‖ Knowledge-Based Syst., vol. 78, pp. 13–21, 2015.
6. R. Pourmoayed, L. R. Nielsen, and A. R. Kristensen, ―A hierarchical
Markov decision process modeling feeding and marketing decisions of
growing pigs,‖ Eur. J. Oper. Res., vol. 250, no. 3, pp. 925–938, 2016.
7. K. S. Gayathri, K. S. Easwarakumar, and S. Elias, ―Probabilistic ontology based activity recognition in smart homes using Markov
Logic Network,‖ Knowledge-Based Syst., vol. 121, pp. 173–184,
2017.
8. Jayasudha, R., Nandini, A., Praveen, N. R., & Prabhakaran, G., (2015). "Cloud Based Inventory Control System for Ration Shop Versatile Management". International Journal of Advanced Scientific Research & Development (IJASRD), 2 (1/I), pp. 41 - 47.
9. Buyya R, Ranjan R, Calheiros R N. Intercloud: Utility-oriented
federation of cloud computing environments for scaling of application
services.Algorithms and architectures for parallel processing. Springer Berlin Heidelberg(2010)13-31.
10. Li W, PING L, LI J. Cloud service discovery algorithm based on trust
fuzzy comprehensive evaluation. ICIC express letters. an international
journal of research and surveys. Part B,
Applications.3(2)(2012)331-336.
11. Zhenji Z, Lifa W, Zheng H, et al. Trust based trustworthiness
attestation model of virtual machines for cloud computing. Journal of Southeast University (Natural Science Edition) 1(007)(2015) 31-35. 12. Sangeetha, B., Saranya, E., & Saranya, G., (2015). "A Novel
Framework for Secure Sharing of Personal Health Records (PHR) in Cloud Computing". International Journal of Advanced Scientific Research & Development (IJASRD), 2 (2/I), pp. 08 - 14.
13. V. Ivey. Five tips to keep your data secure on the Cloud [online](2013).
14. TrueCrypt. TrueCrypt [online] (2014).
15. Spideroak. Spideroak [online] (2014).
16. M. Campi, G. Calafiore, Decision making in an uncertain
environment: the scenario-based optimization approach, Multiple Participant Decision Making (2004) 99–111.
17. Maheswari, A., Sanjana, R., Sowmiya, S., Shenai, S., & Prabhakaran,
G., (2016). "An Efficient Cloud Security System Using Double Secret Key Decryption Process for Secure Cloud Environments". International Journal of Advanced Scientific Research & Development (IJASRD), 3 (1/II), pp. 134 - 139.
18. H. Haas, A. Brown, Web services glossary, W3CWorking Group Note
(11 February 2004) 9.
19. B. Kepes. Understanding the cloud computing stack: Saas, paas, iaas
[online] (October 2013).
20. Stratecast., Tips for choosing a cloud service provider, Tech.Rep.
MSU-CSE-00-2, Department of Science and Technology
21. S. Sun, L. Wang, R. Ranjan, A. Wu, Semantic analysis and retrieval of
spatial data based on the uncertain ontology model in digital earth, Int.
J. Digit. Earth 8 (1) (2015) 3–16. arXiv:
http://dx.doi.org/10.1080/17538947.2014.927538,
doi:10.1080/17538947.2014.927538. URL
http://dx.doi.org/10.1080/17538947.2014.927538
22. C. Esposito, M. Ficco, F. Palmieri, A. Castiglione, Smart cloud storage
service selection based on fuzzy logic, theory of evidencen and game
theory, IEEE T. Comput. PP (99) (2015) 1–1. doi:
10.1109/TC.2015.2389952.
23. R. Csutora, J. J. Buckley, Fuzzy hierarchical analysis: the
Lambda-Max method, Fuzzy Set. Syst. 120 (2) (2001) 181–195. 24. Hema, A., Visalatchy, S., Mallika, C., & Ilakkiya, N., (2017). "A
Survey Paper on Cloud Computing Security and Outsourcing Data Mining in Cloud Platform". International Journal of Advanced Scientific Research & Development (IJASRD), 4 (11/II), pp. 75 - 78.
25. L. Sun. Cloud data storage service ontology [online] (2013).
26. H. Dong, F. K. Hussain, E. Chang, A context-aware semantic
similarity model for ontology environments, Concurr. Comp. Pract. E. 23 (5) (2011) 505–524.
AUTHORSPROFILE