Measuring Security for Applications Hosted in Cloud
Full text
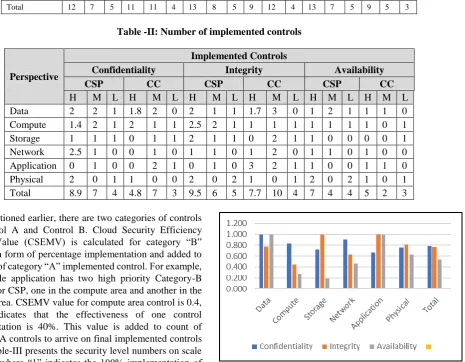
Figure

Related documents
Contract Merger (CM) is an extension of leveraged buyout (LBO), which would be a part of the inorganic growth strategy. Further, it seems to be a ‘Futures Contract’ in the derivatives
Adhesion strength, layer thickness and surface hardness were determined by using ANOVA analysis, while results of rapid deformation test were analyzed by using Kruskal-Wallis
Radiologic parame- ters most frequently found to be associated with symptoms were rotatory subluxation (RS) of the joint and loss of lumbar lordosis leading to global sagittal
Real strides have been made on product innovation with 28% of sales from products that help create a sustainable home, 96% of timber products now responsibly sourced and
Expression profile of genes related to the ascorbate/glutathione pathway (APX, DHAR, and MDHAR), oxidation of polyphenolic compounds (PPO), or biosynthesis of polyphenolic
After this date, users are encouraged to contact the ELSO Guidelines Editorial Board to confirm that this document remains in effect.. On arrival at referring facility,
In the twenty-five years of this statute, which was enacted in 1978 to cover foreign intelligence-gathering within the confines of the United States, no court
Therefore, SWOT matrix with a total of 27 elements was formed in this paper and integrated with the fuzzy PIPRECIA method for assessing the conditions, that is, possibilities,