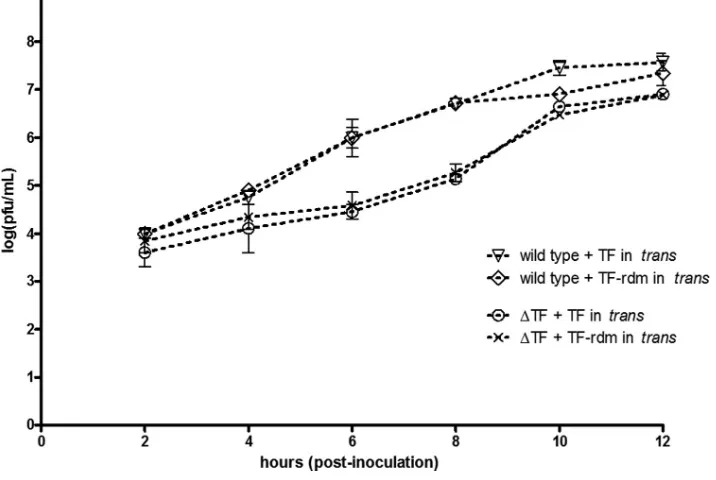
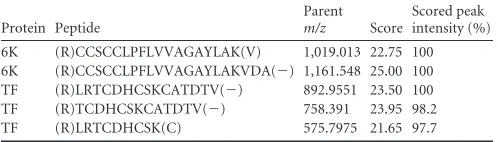
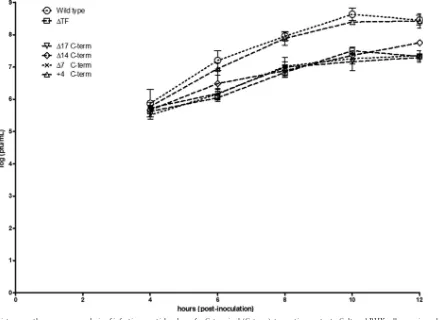
Functional Characterization of the Alphavirus TF Protein
Full text
Figure


Related documents
We study the multi-channel queuing model with ordered entry and state dependent arrival and service rates in order to reduce the backlog, the service rate becomes faster as
Finding 4: Short-term contracts (up to four years, 83%: 4–7 years, 70%) achieved expected cost savings with a higher relative frequency than long-term contracts over seven years,
They like taking pictures and have lots of photo collections.. They put pictures in
In the present work, an analysis of the f E b s -frequency is performed for some tens of earthquakes with magnitudes M > 5.0 by using data of the Japanese vertical
The results indicate that respondents gener - ally had positive attitudes towards inclusion; there were differences between them, depending on the roles they undertook at the
I am conducting research on adjunct faculty job satisfaction levels and professional development interests. You are invited to participate in this study by completing an
The development of the artificial kidney adopted from Kolff by Merrill, Walter, and Thorn was a necessary prerequisite for attempts at transplantation in patients with
In this paper, we initiate the systematic study of NIKE in the public key setting, providing: models and their relationships; constructions for secure NIKE in the Random Oracle