Vehicle Theft Intimation Using GSM
Full text
Figure
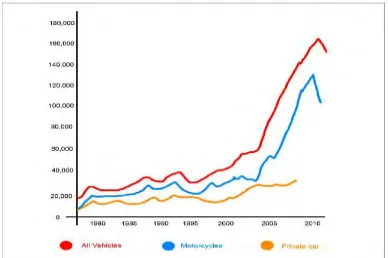

Related documents
If the prospectus either does not qualify as a prospectus published in accordance with the requirements of the EUPD or is not filed with or notified to the relevant
Conversely, where the loss to the victim/s is less than $10,000, but a sentence of more than a year will be imposed, a plea to an offense involving fraud or deceit should
No decorrer dos dez meses de estágio curricular no departamento de Revenue Management no grupo Tivoli Hotels & Resorts, foi-me proposto enquanto complemento há
Infraestructura del Perú INTERNEXA REP Transmantaro ISA Perú TRANSNEXA, 5% investment through INTERNEXA and 45% through INTERNEXA (Perú) COLOMBIA ARGENTINA CENTRAL AMERICA
b In cell B11, write a formula to find Condobolin’s total rainfall for the week.. Use Fill Right to copy the formula into cells C11
Examples raised by focus group participants included working more effectively with institutional research offices to pull better data, working with the career services office to
The ethanol extract of henna leaves 400 mg/kg BW with a dose of leaf ethanol significantly decreased the blood glucose level of wistar mice and there was no
• Server is the computer that stores the web page – Web server, file server, mail server. • Client is the computer that accesses the