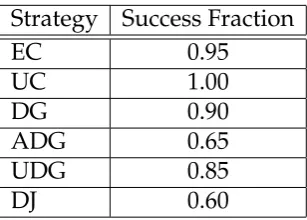
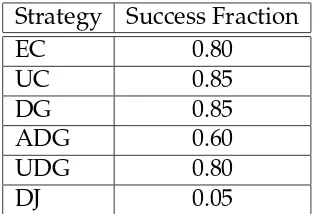
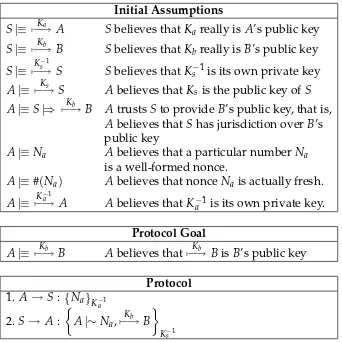
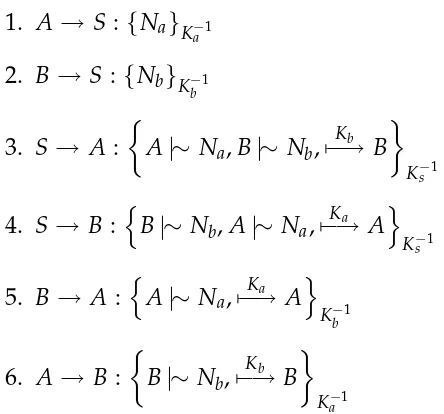A search-based approach to the automated design of security protocols
Full text
Figure
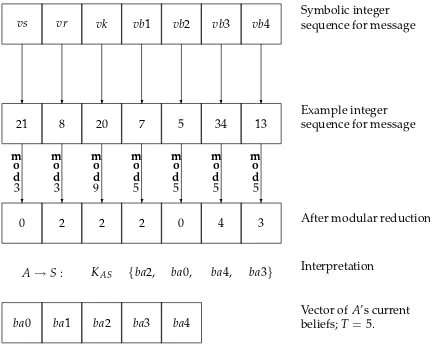
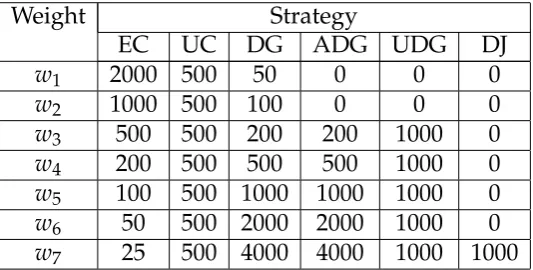
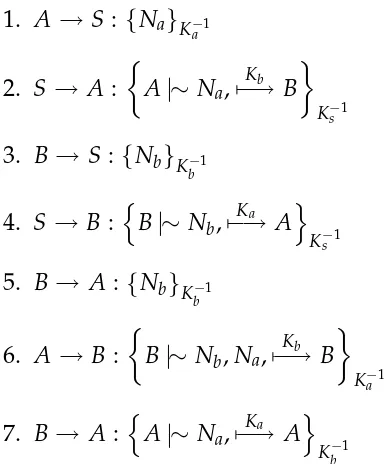
Related documents
Results suggest that the probability of under-educated employment is higher among low skilled recent migrants and that the over-education risk is higher among high skilled
Marie Laure Suites (Self Catering) Self Catering 14 Mr. Richard Naya Mahe Belombre 2516591 info@marielauresuites.com 61 Metcalfe Villas Self Catering 6 Ms Loulou Metcalfe
National Conference on Technical Vocational Education, Training and Skills Development: A Roadmap for Empowerment (Dec. 2008): Ministry of Human Resource Development, Department
Field experiments were conducted at Ebonyi State University Research Farm during 2009 and 2010 farming seasons to evaluate the effect of intercropping maize with
19% serve a county. Fourteen per cent of the centers provide service for adjoining states in addition to the states in which they are located; usually these adjoining states have
• Follow up with your employer each reporting period to ensure your hours are reported on a regular basis?. • Discuss your progress with
taxpayers. Even if the taxpayer is exempt from US estate tax or is taxable at a low level, the taxpayer must provide information on the amount and value of the worldwide estate as
The house, built in 1911, is an early Vancouver home, valued for its association with the growth and development of the Cedar Cottage neighbourhood, once part of the